“Zero-Knowledge Proofs: Unveiling Secrets Without Revealing Them
Related Articles Zero-Knowledge Proofs: Unveiling Secrets Without Revealing Them
- Cloud Data Management Platforms
- Proof Of Stake (PoS): A Comprehensive Overview
- Cryptocurrency: A Comprehensive Guide To The Digital Revolution
- Virtual Data Center Vs Cloud
- Data Cloud Solutions
Introduction
On this special occasion, we are happy to review interesting topics related to Zero-Knowledge Proofs: Unveiling Secrets Without Revealing Them. Let’s knit interesting information and provide new insights to readers.
Table of Content
Zero-Knowledge Proofs: Unveiling Secrets Without Revealing Them
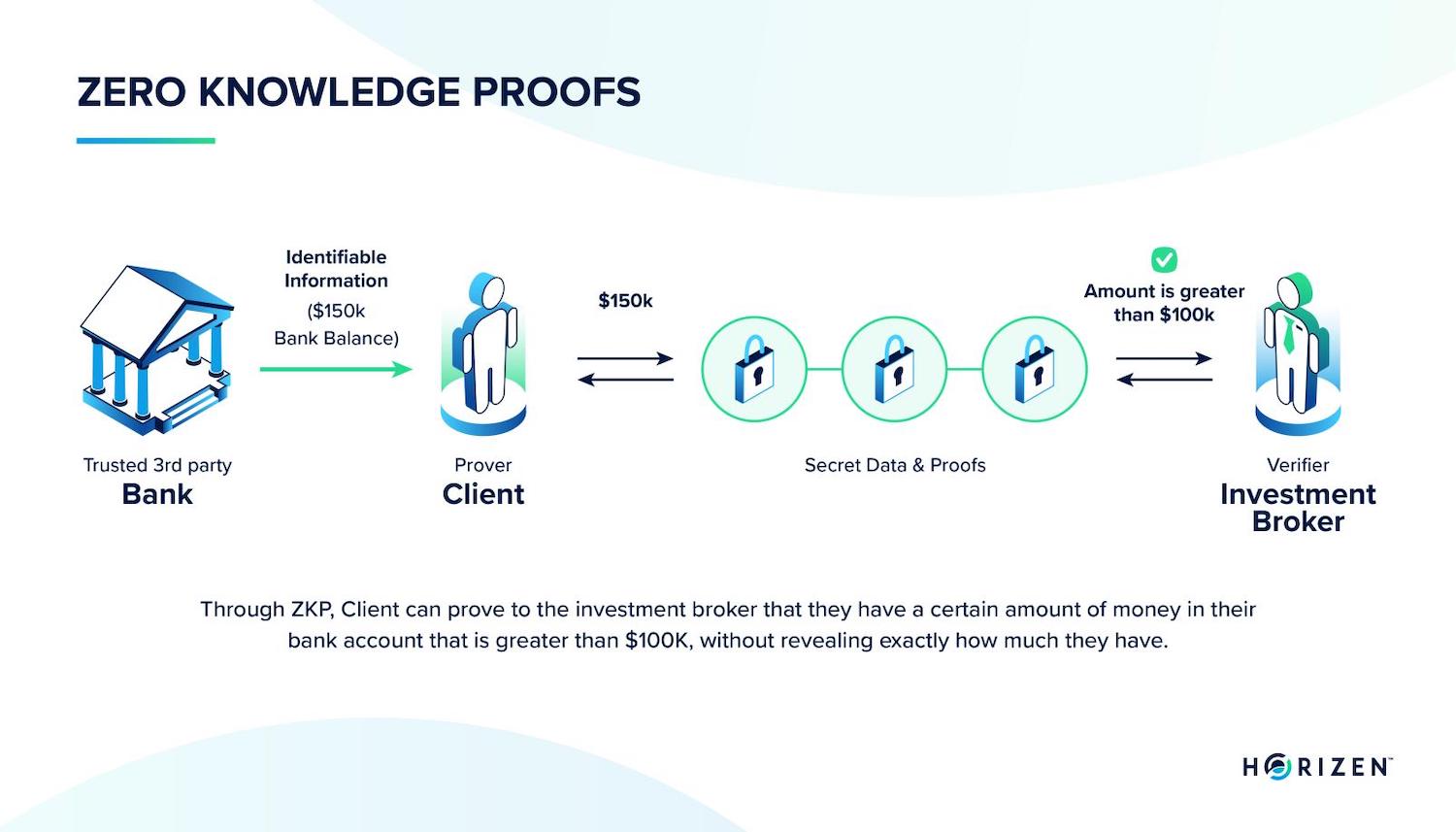
In the realm of cryptography and computer science, the concept of proving knowledge without revealing the knowledge itself might seem like a paradox. Yet, this is precisely what zero-knowledge proofs (ZKPs) accomplish. ZKPs are cryptographic protocols that allow one party (the prover) to convince another party (the verifier) that a statement is true, without conveying any information beyond the veracity of the statement. This seemingly magical feat has profound implications for privacy, security, and trust in various domains.
Understanding the Core Principles
At its heart, a zero-knowledge proof relies on a carefully orchestrated interaction between the prover and the verifier. To qualify as a true ZKP, a protocol must satisfy three key properties:
-
Completeness: If the statement is true, an honest prover can convince an honest verifier that it is true.
-
Soundness: If the statement is false, no prover can convince an honest verifier that it is true, except with a negligible probability.
-
Zero-Knowledge: The verifier learns nothing beyond the fact that the statement is true. In other words, the verifier gains no information that would help them prove the statement to someone else, or learn anything about the secret itself.
The Classic Cave Analogy
One of the most intuitive ways to grasp the concept of ZKPs is through the classic "Ali Baba’s Cave" analogy, originally proposed by Jean-Jacques Quisquater and colleagues.
Imagine a cave shaped like a ring, with two entrances, A and B, and a secret door in the middle that can only be opened with a magic word. Peggy (the prover) wants to convince Victor (the verifier) that she knows the magic word without revealing it.
Here’s how the zero-knowledge proof works:
-
Peggy enters the cave through entrance A or B, chosen randomly.
-
Victor waits outside and then shouts, "Come out from entrance A!" or "Come out from entrance B!" (He chooses randomly).
-
If Peggy knows the magic word, she can always comply with Victor’s request, opening the secret door if necessary.
-
They repeat this process multiple times.
If Peggy didn’t know the magic word, she would only have a 50% chance of correctly exiting the entrance Victor requested each time. After repeating the process, say, 20 times, the probability of her successfully completing the proof without knowing the magic word becomes astronomically small.
Crucially, Victor learns nothing about the magic word itself. He only gains confidence that Peggy knows it.
Types of Zero-Knowledge Proofs
ZKPs come in various flavors, each with its own strengths and weaknesses:
-
Interactive Zero-Knowledge Proofs: These proofs involve a back-and-forth exchange of information between the prover and the verifier, as demonstrated in the Ali Baba’s Cave example.
-
Non-Interactive Zero-Knowledge Proofs (NIZK): In NIZK proofs, the prover can generate a proof that the verifier can check without any interaction. This is often achieved using a common reference string (CRS), which is assumed to be generated randomly and made available to both parties.
-
Zero-Knowledge Succinct Non-Interactive Argument of Knowledge (zk-SNARKs): zk-SNARKs are a particularly powerful type of NIZK proof that are both succinct (the proof size is small) and efficient to verify. They are widely used in blockchain and privacy-preserving applications.
-
Zero-Knowledge Scalable Transparent ARguments of Knowledge (zk-STARKs): zk-STARKs are another type of NIZK proof that offer similar advantages to zk-SNARKs but are considered more transparent because they don’t rely on a trusted setup (the CRS can be generated without requiring a trusted third party).
Applications of Zero-Knowledge Proofs
The potential applications of ZKPs are vast and span numerous industries:
-
Blockchain and Cryptocurrency:
- Privacy-Preserving Transactions: ZKPs can enable transactions where the sender, receiver, and amount are hidden from public view, while still allowing network participants to verify that the transaction is valid (e.g., the sender has sufficient funds). Zcash is a prominent example of a cryptocurrency that uses zk-SNARKs for this purpose.
- Scalability: ZKPs can be used to compress multiple transactions into a single proof, which can then be verified by the blockchain. This can significantly improve the scalability of blockchain networks.
- Decentralized Identity: ZKPs can allow users to prove claims about their identity (e.g., age, citizenship) without revealing the underlying data to the verifier.
-
Authentication and Access Control:
- Passwordless Authentication: ZKPs can be used to authenticate users without requiring them to store or transmit passwords. The user can prove that they know the password without actually revealing it to the server.
- Attribute-Based Access Control: ZKPs can enable access control policies based on attributes (e.g., role, security clearance) without revealing the specific attributes to the system.
-
Secure Computation:
- Private Data Analysis: ZKPs can allow parties to perform computations on sensitive data without revealing the data to each other. For example, multiple hospitals could collaborate to analyze patient data without revealing the individual records.
- Verifiable Machine Learning: ZKPs can be used to prove that a machine learning model was trained correctly and that its predictions are accurate, without revealing the model or the training data.
-
Supply Chain Management:
- Provenance Tracking: ZKPs can be used to track the origin and history of products without revealing sensitive information about suppliers or manufacturers.
- Compliance Verification: ZKPs can be used to verify that products meet certain standards or regulations without revealing the underlying data.
-
Voting Systems:
- Secure and Verifiable Elections: ZKPs can be used to create voting systems that are both secure and verifiable. Voters can prove that they cast their ballot correctly, and anyone can verify that the election results are accurate, without revealing how individual voters voted.
Challenges and Future Directions
Despite their immense potential, ZKPs also face several challenges:
- Computational Complexity: Generating ZKPs can be computationally intensive, especially for complex statements.
- Trusted Setup: Some ZKP schemes, such as zk-SNARKs, require a trusted setup to generate the common reference string (CRS). If the setup is compromised, the security of the proof system can be compromised.
- Standardization: There is a lack of standardization in ZKP protocols, which can hinder interoperability and adoption.
- Complexity for Developers: Implementing ZKPs can be complex and requires specialized knowledge.
Future research directions in ZKPs include:
- Improving Efficiency: Developing more efficient ZKP protocols that require less computation and communication.
- Eliminating Trusted Setup: Developing ZKP schemes that do not require a trusted setup, such as zk-STARKs.
- Developing Tooling and Libraries: Creating developer-friendly tools and libraries that make it easier to implement ZKPs.
- Exploring New Applications: Discovering new and innovative applications of ZKPs in various domains.
Conclusion
Zero-knowledge proofs are a powerful cryptographic tool that enables parties to prove knowledge without revealing the knowledge itself. Their unique properties have profound implications for privacy, security, and trust in various applications, including blockchain, authentication, secure computation, and supply chain management. While challenges remain, ongoing research and development efforts are paving the way for wider adoption of ZKPs and unlocking their full potential to revolutionize the way we interact with data and systems. As the world becomes increasingly data-driven, the ability to prove facts without revealing sensitive information will become ever more crucial, making zero-knowledge proofs a cornerstone of a more secure and privacy-respecting future.

