“What Is a Honeypot in Crypto? How to Spot and Avoid These Traps
Related Articles What Is a Honeypot in Crypto? How to Spot and Avoid These Traps
- How Blockchain Helps In Humanitarian Aid: Transforming Trust, Transparency, And Efficiency
- Best Private Student Loans and Current Rates of August 2022
- Smart Contracts: Revolutionizing Trust And Automation In The Digital Age
- Arbitrum: A Deep Dive Into Layer-2 Scaling For Ethereum
- Okay, Here’s A Comprehensive Article About Boiling Eggs, Covering Various Aspects From Timing To Troubleshooting, Aiming For Around 1600 Words.
Introduction
On this special occasion, we are happy to review interesting topics related to What Is a Honeypot in Crypto? How to Spot and Avoid These Traps. Let’s knit interesting information and provide new insights to readers.
Table of Content
What Is a Honeypot in Crypto? How to Spot and Avoid These Traps
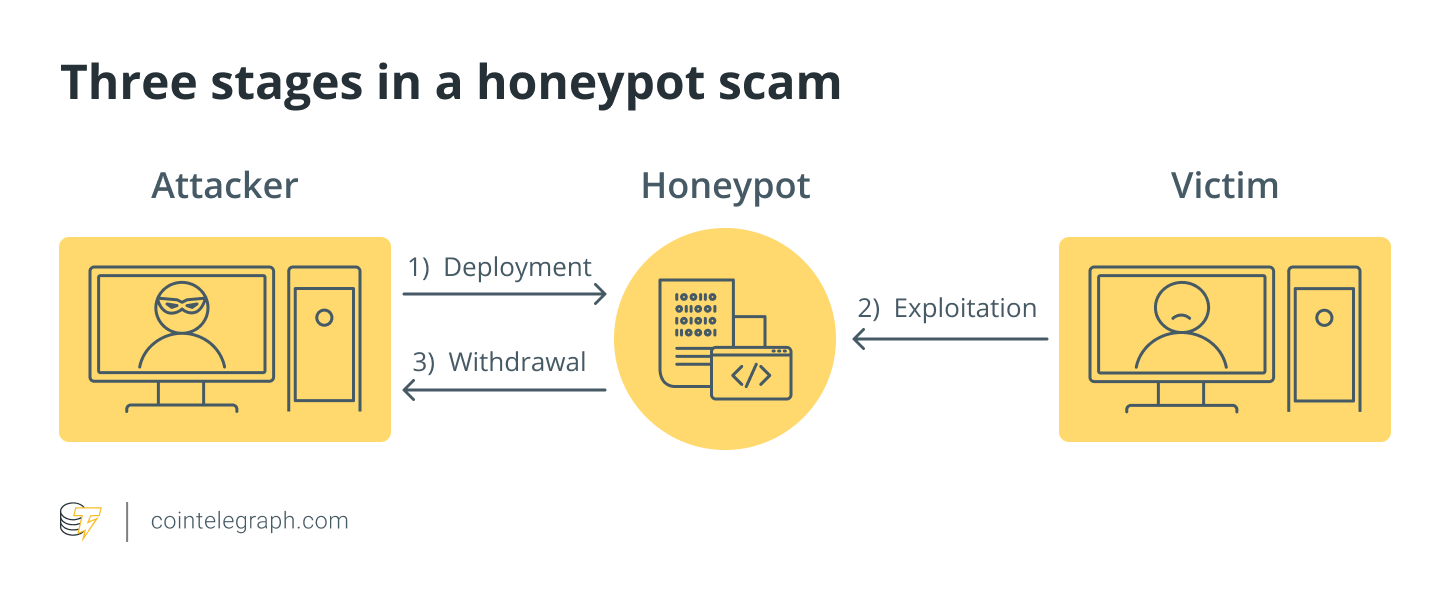
The world of cryptocurrencies and decentralized finance (DeFi) is rife with opportunities for innovation and profit. However, it also attracts malicious actors looking to exploit unsuspecting investors. Among the most insidious traps is the "honeypot" – a type of smart contract designed to appear legitimate but ultimately steals your funds. Understanding how honeypots work, and how to identify them, is crucial for anyone participating in the crypto space.
What is a Honeypot in Crypto?
In cybersecurity, a honeypot is a decoy system designed to attract and trap hackers. In the crypto world, a honeypot is a smart contract that appears to be a legitimate token or DeFi project, but it contains hidden vulnerabilities that allow the creator to drain funds from unsuspecting users.
The basic premise is simple: a user sees a new, promising token or project, often advertised with high potential returns. They invest their cryptocurrency to buy the token, but when they try to sell it back, they find they are unable to do so. The honeypot creator has designed the contract in such a way that only they can withdraw funds.
How Crypto Honeypots Work: A Technical Deep Dive
Honeypots exploit the complexity of smart contracts, which are self-executing agreements written in code and deployed on blockchains like Ethereum. These contracts govern the rules of a token, including how it can be bought, sold, and transferred.
Here’s a breakdown of the most common honeypot mechanisms:
- The Unsellable Token: This is the most common type of honeypot. The smart contract is designed so that anyone can buy the token, but only the creator (or a designated address) can sell it. This is achieved through various coding tricks:
- Blacklisting: The contract may contain a hidden function that allows the creator to blacklist certain addresses, preventing them from selling.
- Transfer Restrictions: The contract may impose restrictions on transfers, such as requiring the seller to hold a certain amount of another token, which is impossible to obtain.
- High Slippage Manipulation: Setting artificially high slippage tolerances that drain most of the value during the sell transaction.
- Hidden Ownership: The contract’s ownership is transferred to an address that no one controls, effectively locking the token forever.
- The Malicious Function: Some honeypots contain malicious functions that are triggered when a user interacts with the contract. These functions can:
- Approve Spending: Grant the honeypot creator unlimited access to your wallet, allowing them to drain your funds.
- Transfer Funds: Secretly transfer your funds to the creator’s address.
- Selfdestruct: Destroy the contract and all the tokens within it, making them worthless.
- The False Deposit: A user deposits funds into a DeFi protocol, only to discover that the protocol is designed to steal their deposit. This can be achieved through:
- Fake Rewards: The protocol promises high rewards but never pays them out.
- Hidden Fees: The protocol charges exorbitant fees for withdrawals, effectively trapping your funds.
- Backdoor Access: The creator has a backdoor that allows them to withdraw all the funds from the protocol.
Why Are Honeypots So Effective?
Honeypots are effective because they exploit several factors:
- Greed: The promise of high returns can cloud people’s judgment, making them less likely to scrutinize the project.
- Complexity: Smart contracts can be complex and difficult to understand, even for experienced developers. This makes it easy for malicious code to hide in plain sight.
- Lack of Regulation: The crypto space is still largely unregulated, making it difficult to hold honeypot creators accountable.
- FOMO (Fear of Missing Out): The hype around new tokens and projects can create a sense of urgency, leading people to invest without doing their due diligence.
How to Identify and Avoid Crypto Honeypots
While honeypots can be sophisticated, there are several red flags that can help you spot them:
-
Analyze the Smart Contract Code:
- Verify the Source Code: Check if the contract’s source code has been verified on a blockchain explorer like Etherscan. Verified code is more likely to be legitimate.
- Read the Code: If you have programming experience, carefully read the code. Look for suspicious functions, hidden logic, or unusual restrictions.
- Use Automated Tools: Several tools can automatically scan smart contracts for common vulnerabilities. Some popular options include Mythril, Slither, and Oyente.
-
Check Token Liquidity:
- Low Liquidity: If the token has very low liquidity on decentralized exchanges (DEXs) like Uniswap or PancakeSwap, it may be difficult to sell.
- Uneven Liquidity Distribution: If the creator holds a disproportionately large share of the liquidity pool, they could potentially manipulate the price or drain the pool.
-
Review Transaction History:
- Suspicious Transactions: Look for unusual patterns in the transaction history, such as large transfers to unknown addresses or frequent changes to the contract’s code.
- Creator Activity: Check the creator’s address for other suspicious activity, such as creating multiple honeypots or interacting with known scam addresses.
-
Examine the Project’s Website and Social Media:
- Lack of Information: Be wary of projects with little or no information about the team, the technology, or the project’s goals.
- Unprofessional Website: A poorly designed or unprofessional website can be a sign of a scam.
- Fake Social Media Engagement: Look for signs of fake followers, bots, or paid promotion on social media.
-
Test the Sell Functionality:
- Small Test Transaction: Before investing a significant amount of money, try buying and selling a small amount of the token. If you are unable to sell, it’s a clear sign of a honeypot.
- Slippage Issues: If the slippage required to sell the token is excessively high, it may be a sign that the contract is designed to drain your funds.
-
Use Honeypot Detection Tools:
- Token Sniffer: Websites like Token Sniffer analyze tokens and provide a risk assessment based on various factors, including code analysis, liquidity, and transaction history.
- IsThisaScam: This tool helps identify potential scams, including honeypots, by analyzing the token’s smart contract and other data.
-
Community Vetting:
- Consult Crypto Communities: Ask for opinions and reviews on crypto forums, Reddit, and Telegram groups. Often, experienced members can identify red flags that you might miss.
Examples of Notorious Crypto Honeypots
- Squid Game Token (SQUID): Capitalizing on the popularity of the Netflix series, this token promised high returns but turned out to be a honeypot. Investors could buy the token but were unable to sell it, resulting in significant losses.
- Save The Kids Token (SAVE): Marketed as a charity token, this project was later revealed to be a honeypot. The creators drained the liquidity pool, leaving investors with worthless tokens.
Best Practices for Staying Safe
- Do Your Own Research (DYOR): Never invest in a project without thoroughly researching it.
- Invest Only What You Can Afford to Lose: The crypto market is volatile, and even legitimate projects can fail.
- Be Skeptical of High Returns: If a project promises unrealistic returns, it’s likely a scam.
- Use a Hardware Wallet: Store your cryptocurrency in a hardware wallet to protect it from online attacks.
- Enable Two-Factor Authentication (2FA): Use 2FA on all your crypto accounts to prevent unauthorized access.
- Stay Informed: Keep up to date on the latest scams and security threats in the crypto space.
Conclusion
Crypto honeypots are a serious threat to investors, but by understanding how they work and taking precautions, you can significantly reduce your risk. Remember to always do your own research, be skeptical of high returns, and carefully analyze the smart contract code before investing in any new token or project. The crypto space is full of opportunities, but it’s also full of risks. By staying vigilant and informed, you can protect yourself from becoming a victim of a honeypot scam.

