“Proof of Work (PoW): The Foundation of Blockchain Security
Related Articles Proof of Work (PoW): The Foundation of Blockchain Security
- fbs forex
- HODL: The Accidental Mantra That Defined A Generation Of Crypto Investors
- Retrieve Data From Cloud
- car insurance 800 a year
- xm global mt4
Introduction
With great enthusiasm, let’s explore interesting topics related to Proof of Work (PoW): The Foundation of Blockchain Security. Come on knit interesting information and provide new insights to readers.
Table of Content
Proof of Work (PoW): The Foundation of Blockchain Security
In the ever-evolving landscape of blockchain technology, Proof of Work (PoW) stands as a foundational consensus mechanism, the linchpin of security and decentralization for many prominent cryptocurrencies, most notably Bitcoin. This article delves into the intricacies of PoW, exploring its origins, functionality, strengths, weaknesses, and its ongoing relevance in the face of newer consensus algorithms.
Origins and Conceptual Basis
The concept of Proof of Work predates Bitcoin, with roots in the fight against spam emails and Distributed Denial of Service (DDoS) attacks. In 1993, Cynthia Dwork and Moni Naor introduced the idea of requiring senders to perform a computationally intensive task before sending an email, making mass spamming economically unfeasible.
Later, in 1999, Markus Jakobsson and Ari Juels formalized the term "Proof of Work" in a paper, further solidifying its conceptual framework. However, it was Satoshi Nakamoto’s incorporation of PoW into the Bitcoin blockchain in 2008 that catapulted it to prominence.
At its core, PoW is a mechanism that requires participants (miners) in a blockchain network to expend computational effort to solve a complex mathematical puzzle. The solution to this puzzle serves as "proof" that the miner has invested resources and time, making it costly to manipulate the blockchain.
How Proof of Work Functions
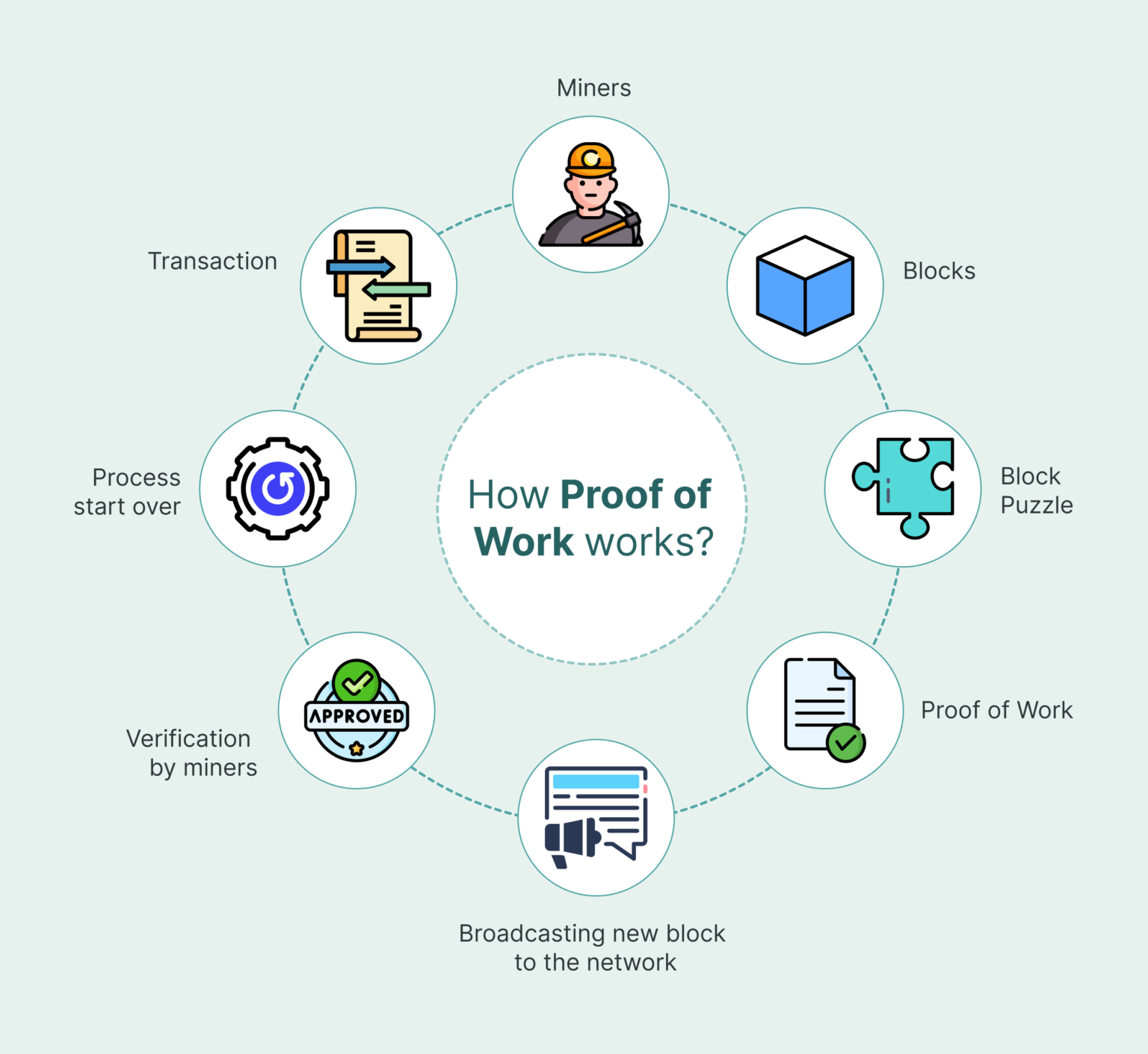
- Transaction Aggregation: Transactions on the blockchain are bundled together into blocks.
- The Mining Process: Miners compete to find a hash value for the block that meets specific criteria set by the network. This involves repeatedly modifying a nonce (a random number) within the block data and recalculating the hash until a valid solution is found.
- The Hash Puzzle: The "puzzle" is to find a hash that is below a certain target value. The target value is dynamically adjusted by the network to maintain a consistent block creation rate. The lower the target, the harder it is to find a valid hash.
- Computational Effort: The only way to find a valid hash is through brute-force computation, trying different nonce values until one produces a hash that meets the target. This requires significant computational power and energy consumption.
- Block Validation and Consensus: Once a miner finds a valid hash, they broadcast the block to the network. Other nodes verify that the hash is indeed valid and that the block adheres to the blockchain’s rules. If the block is valid, it is added to the chain.
- Reward and Incentive: The miner who successfully solves the puzzle and adds a new block to the chain is rewarded with newly minted cryptocurrency (e.g., Bitcoin) and transaction fees from the transactions included in the block. This incentivizes miners to participate in the network and maintain its security.
Key Characteristics of Proof of Work
- Computational Intensity: PoW is designed to be computationally intensive, requiring significant hardware and energy resources.
- Asymmetric Cost: The cost of finding a valid solution is high, but the cost of verifying the solution is low. This asymmetry is crucial for security.
- Difficulty Adjustment: The difficulty of the PoW puzzle is dynamically adjusted to maintain a consistent block creation rate, regardless of the total computational power on the network.
- Incentive Mechanism: The block reward and transaction fees provide a strong economic incentive for miners to participate in the network.
Strengths of Proof of Work
- Security: PoW has proven to be a robust and secure consensus mechanism. It is resistant to various attacks, including Sybil attacks (where an attacker creates multiple identities to gain control) and double-spending attacks (where an attacker attempts to spend the same cryptocurrency twice).
- Decentralization: PoW promotes decentralization by allowing anyone with the necessary hardware and energy resources to participate in mining.
- Proven Track Record: Bitcoin, the most successful cryptocurrency, relies on PoW, demonstrating its effectiveness in securing a large-scale blockchain network.
- Simplicity: The underlying concept of PoW is relatively simple to understand, which contributes to its widespread adoption.
Weaknesses of Proof of Work
- Energy Consumption: PoW is notorious for its high energy consumption, which has raised environmental concerns.
- Centralization of Mining Power: Over time, mining has become increasingly concentrated in the hands of large mining pools, which can threaten the decentralization of the network.
- 51% Attack Vulnerability: If a single entity or group gains control of more than 50% of the network’s computational power, they could potentially manipulate the blockchain and perform double-spending attacks.
- Scalability Issues: PoW can lead to scalability issues, as the block creation rate is limited by the difficulty of the PoW puzzle. This can result in slow transaction processing times and high transaction fees.
- Hardware Specialization: The development of specialized mining hardware (ASICs) has created an arms race, making it difficult for individuals with general-purpose computers to participate in mining.
Alternatives to Proof of Work
Due to the limitations of PoW, numerous alternative consensus mechanisms have emerged, each with its own trade-offs:
- Proof of Stake (PoS): PoS relies on validators who "stake" their cryptocurrency to secure the network. Validators are chosen to create new blocks based on the amount of cryptocurrency they stake and other factors. PoS is generally more energy-efficient than PoW, but it has its own challenges, such as the "nothing at stake" problem.
- Delegated Proof of Stake (DPoS): DPoS involves electing a smaller number of delegates to validate transactions and create new blocks. DPoS is typically faster and more scalable than PoW, but it can be more centralized.
- Proof of Authority (PoA): PoA relies on a small number of trusted validators to secure the network. PoA is highly efficient and scalable, but it is also highly centralized.
- Other Variants: There are many other variants of consensus mechanisms, such as Proof of Burn (PoB), Proof of Capacity (PoC), and hybrid approaches that combine elements of different mechanisms.
The Future of Proof of Work
Despite its drawbacks, Proof of Work remains a relevant and important consensus mechanism in the blockchain space. Bitcoin’s continued dominance and security are a testament to its effectiveness. However, the environmental concerns and scalability issues associated with PoW have led to ongoing research and development of alternative consensus mechanisms.
It is likely that PoW will continue to be used in some blockchain networks, particularly those that prioritize security and decentralization above all else. However, other consensus mechanisms, such as Proof of Stake, may become more prevalent in networks that require greater energy efficiency and scalability.
Conclusion
Proof of Work has played a pivotal role in the development and adoption of blockchain technology. It has proven to be a robust and secure consensus mechanism, but it also has significant limitations, particularly in terms of energy consumption and scalability. As the blockchain space continues to evolve, it is likely that we will see a mix of different consensus mechanisms, each tailored to the specific needs and priorities of the network. PoW’s legacy as the pioneering consensus mechanism will undoubtedly continue to shape the future of blockchain technology.