“Phishing Scams: How to Identify and Protect Yourself From These Cyber Threats
Related Articles Phishing Scams: How to Identify and Protect Yourself From These Cyber Threats
- 3d Point Cloud Data
- forex simulator
- Why Move Data To The Cloud
- Salesforce Marketing Cloud Data
- Best Buy: A Retail Giant Navigating The Evolving Landscape Of Consumer Electronics
Introduction
We will be happy to explore interesting topics related to Phishing Scams: How to Identify and Protect Yourself From These Cyber Threats. Come on knit interesting information and provide new insights to readers.
Table of Content
Phishing Scams: How to Identify and Protect Yourself From These Cyber Threats

In today’s digital age, where technology has become an integral part of our daily lives, the internet has opened up a world of opportunities for communication, commerce, and information sharing. However, this interconnectedness has also given rise to various online threats, with phishing scams being one of the most prevalent and dangerous. Phishing is a type of cybercrime that involves deceiving individuals into divulging sensitive information, such as usernames, passwords, credit card details, and other personal data, by disguising oneself as a trustworthy entity.
In this comprehensive article, we will delve into the intricacies of phishing scams, exploring their various forms, the techniques employed by cybercriminals, and, most importantly, the measures you can take to identify and protect yourself from falling victim to these deceptive schemes. By understanding the nature of phishing scams and adopting proactive security practices, you can significantly reduce your risk of becoming a target and safeguard your valuable information.
Understanding the Anatomy of a Phishing Scam
At its core, a phishing scam is a deceptive attempt to acquire sensitive information by masquerading as a legitimate organization or individual. Cybercriminals often employ social engineering techniques to manipulate their victims into divulging their personal data. These techniques exploit human psychology, preying on emotions such as fear, urgency, or greed to trick individuals into taking actions they would not normally take.
Phishing scams typically involve the following key elements:
- Deceptive Communication: Phishing scams often begin with a deceptive email, text message, or phone call that appears to be from a reputable source, such as a bank, credit card company, government agency, or popular online service. The communication typically contains a sense of urgency or threat, prompting the recipient to take immediate action.
- Imitation of Legitimate Organizations: Cybercriminals go to great lengths to mimic the appearance and branding of legitimate organizations. They may use the company’s logo, colors, and language to create a sense of authenticity. The email or website may even contain links to legitimate pages on the company’s website, further enhancing the illusion of legitimacy.
- Request for Sensitive Information: The primary goal of a phishing scam is to obtain sensitive information from the victim. The communication may request the recipient to update their account details, verify their identity, or confirm a transaction. The request may be disguised as a routine security measure or a necessary step to avoid account suspension or other negative consequences.
- Malicious Links or Attachments: Phishing scams often contain malicious links or attachments that, when clicked or opened, can install malware on the victim’s computer or redirect them to a fake website that resembles the legitimate one. These fake websites are designed to steal the victim’s login credentials or other personal information.
Common Types of Phishing Scams
Phishing scams come in various forms, each designed to target specific individuals or organizations. Here are some of the most common types of phishing scams:
- Email Phishing: Email phishing is the most common type of phishing scam. Cybercriminals send deceptive emails that appear to be from legitimate organizations, requesting sensitive information or directing the recipient to a fake website.
- Spear Phishing: Spear phishing is a more targeted form of phishing that focuses on specific individuals or organizations. Cybercriminals gather information about their targets from publicly available sources, such as social media or company websites, to create highly personalized and convincing phishing emails.
- Whaling: Whaling is a type of spear phishing that targets high-profile individuals, such as CEOs or other senior executives. Cybercriminals often impersonate other executives or trusted business partners to gain access to sensitive company information.
- Smishing: Smishing is a type of phishing that uses text messages to trick victims into divulging their personal information. Cybercriminals may send text messages that appear to be from banks, credit card companies, or other organizations, requesting the recipient to verify their account details or click on a malicious link.
- Vishing: Vishing is a type of phishing that uses phone calls to deceive victims into providing their personal information. Cybercriminals may impersonate customer service representatives, government officials, or other trusted individuals to gain the victim’s trust.
- Pharming: Pharming is a more sophisticated type of phishing that involves redirecting victims to fake websites without their knowledge. Cybercriminals may compromise DNS servers to redirect users to malicious websites, even if they type the correct URL.
How to Identify Phishing Scams
While phishing scams can be sophisticated and difficult to detect, there are several red flags that can help you identify them:
- Suspicious Sender Address: Check the sender’s email address carefully. Phishing emails often come from addresses that are slightly different from the legitimate organization’s email address. For example, a phishing email may come from "support@bankofamerica.com" instead of "support@bankofamerica.com."
- Generic Greetings: Phishing emails often use generic greetings, such as "Dear Customer" or "Dear Account Holder," instead of addressing you by name.
- Urgent or Threatening Language: Phishing emails often use urgent or threatening language to pressure you into taking immediate action. For example, the email may threaten to suspend your account if you do not update your information immediately.
- Grammatical Errors and Typos: Phishing emails often contain grammatical errors and typos. Legitimate organizations typically have professional writers and editors who proofread their communications carefully.
- Suspicious Links: Hover over links in the email to see where they lead. If the link leads to a website that is different from the legitimate organization’s website, it is likely a phishing scam.
- Requests for Personal Information: Be wary of emails that request personal information, such as your username, password, credit card details, or Social Security number. Legitimate organizations will typically not ask for this information via email.
- Unsolicited Emails: Be suspicious of unsolicited emails, especially if they come from organizations that you do not have a relationship with.
- Inconsistencies in Design or Branding: Phishing emails may have inconsistencies in design or branding, such as outdated logos or mismatched colors.
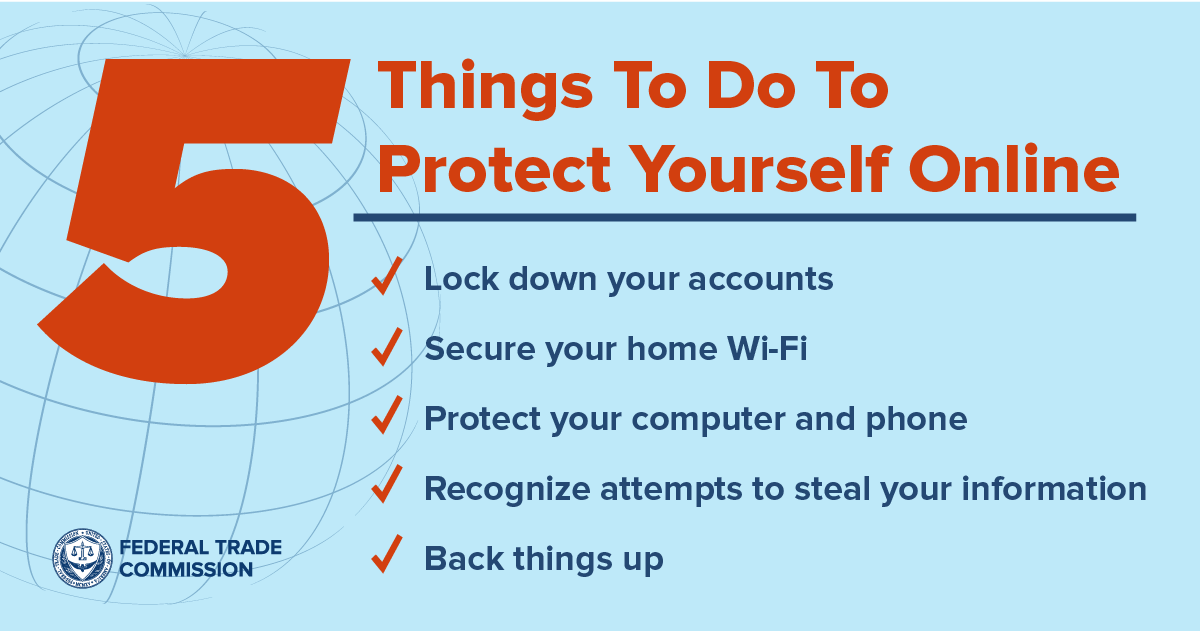
Protecting Yourself From Phishing Scams
Protecting yourself from phishing scams requires a combination of awareness, caution, and proactive security measures. Here are some tips to help you stay safe:
- Be Skeptical of Unsolicited Emails: Be wary of unsolicited emails, especially if they come from organizations that you do not have a relationship with.
- Verify Sender Identity: Before clicking on any links or providing any personal information, verify the sender’s identity by contacting the organization directly. Use a phone number or website address that you know to be legitimate.
- Don’t Click on Suspicious Links: Avoid clicking on links in emails or text messages that you are unsure about. Instead, type the website address directly into your browser.
- Keep Your Software Up to Date: Keep your operating system, web browser, and antivirus software up to date. Software updates often include security patches that protect against phishing attacks.
- Use Strong Passwords: Use strong, unique passwords for all of your online accounts. Avoid using the same password for multiple accounts.
- Enable Two-Factor Authentication: Enable two-factor authentication (2FA) whenever possible. 2FA adds an extra layer of security to your accounts by requiring you to enter a code from your phone or another device in addition to your password.
- Be Careful About Sharing Personal Information: Be careful about sharing personal information online, especially on social media. Cybercriminals can use this information to create more convincing phishing scams.
- Educate Yourself and Others: Stay informed about the latest phishing scams and share your knowledge with family and friends. The more people who are aware of phishing scams, the less likely they are to fall victim to them.
- Report Phishing Scams: If you receive a phishing email or text message, report it to the organization that is being impersonated and to the Federal Trade Commission (FTC).
Conclusion
Phishing scams are a serious threat to individuals and organizations alike. By understanding the nature of phishing scams, knowing how to identify them, and taking proactive security measures, you can significantly reduce your risk of becoming a victim. Remember to be skeptical of unsolicited emails, verify sender identity, avoid clicking on suspicious links, keep your software up to date, use strong passwords, enable two-factor authentication, be careful about sharing personal information, educate yourself and others, and report phishing scams. By following these tips, you can protect yourself and your valuable information from the ever-evolving threat of phishing scams.