“How Phishing Scams Work in Crypto
Related Articles How Phishing Scams Work in Crypto
- Ethereum Gas Fees Plummet After Upgrade: A Deep Dive Into The Factors Behind The Relief
- Temu: The Rise Of Ultra-Fast Fashion And Its Global Impact
- Litecoin: A Deep Dive Into The Silver To Bitcoin’s Gold
- Polkadot: The Internet Of Blockchains, Unlocking The Future Of Web3
- Google: A Titan Of Technology, Innovation, And Information
Introduction
With great enthusiasm, let’s explore interesting topics related to How Phishing Scams Work in Crypto. Let’s knit interesting information and provide new insights to readers.
Table of Content
How Phishing Scams Work in Crypto
In the rapidly evolving world of cryptocurrencies, where digital assets can be transferred across borders in an instant, the potential for financial gain is immense. However, this lucrative landscape has also attracted malicious actors who seek to exploit vulnerabilities in the system for their own profit. One of the most prevalent and insidious methods employed by these cybercriminals is phishing.
Phishing is a type of social engineering attack that aims to deceive individuals into divulging sensitive information, such as usernames, passwords, private keys, or seed phrases, by disguising as a trustworthy entity. In the context of cryptocurrencies, phishing scams can have devastating consequences, leading to the loss of valuable digital assets.
Understanding the Mechanics of Crypto Phishing
To effectively protect yourself from phishing scams in the crypto space, it’s crucial to understand how these attacks are typically executed. The following sections delve into the various tactics and techniques employed by phishers to lure unsuspecting victims.
1. Deceptive Emails and Messages
One of the most common methods used by phishers is sending deceptive emails or messages that appear to originate from legitimate sources, such as cryptocurrency exchanges, wallet providers, or even well-known figures in the crypto community. These messages often contain urgent or alarming content, such as warnings of account compromise, requests for verification, or announcements of exclusive promotions.
The key to identifying phishing emails or messages is to scrutinize the sender’s address. Phishers often use domain names that closely resemble the legitimate organization they are impersonating, with subtle variations that can easily be overlooked. For example, an email claiming to be from "Binance" might actually come from "Binancee" or "Binance-support."
2. Fake Websites and Landing Pages
Phishing emails or messages typically include links that redirect victims to fake websites or landing pages that mimic the appearance of legitimate platforms. These fake websites are designed to trick users into entering their login credentials, private keys, or other sensitive information.
To avoid falling victim to this tactic, always double-check the URL of the website you are visiting. Legitimate websites use HTTPS (Hypertext Transfer Protocol Secure), which encrypts the data transmitted between your browser and the server. Look for the padlock icon in the address bar, indicating that the connection is secure.
3. Social Media Scams
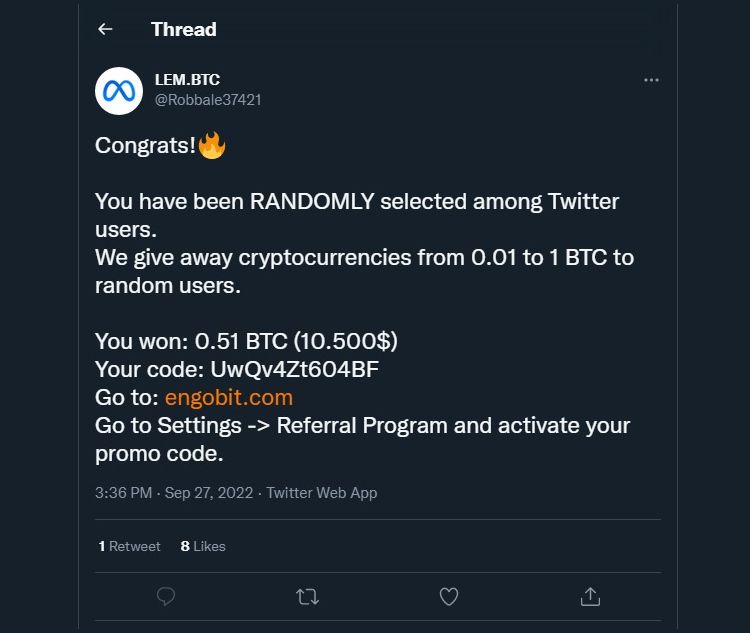
Social media platforms have become fertile ground for phishing scams in the crypto space. Phishers often create fake profiles that impersonate well-known figures or organizations in the crypto community. They then use these profiles to post deceptive messages, links, or promotions that lure unsuspecting users to fake websites or solicit personal information.
Be wary of any unsolicited messages or friend requests from individuals you don’t know, especially if they are offering investment opportunities or promising guaranteed returns. Always verify the legitimacy of social media profiles by checking for verified badges, follower counts, and engagement history.
4. QR Code Scams
QR codes, which are two-dimensional barcodes that can be scanned with a smartphone, have become increasingly popular in the crypto world for facilitating transactions and accessing websites. However, phishers can also exploit QR codes to redirect victims to malicious websites or trigger unauthorized transactions.
Before scanning a QR code, always verify its legitimacy by checking the source and ensuring that it is associated with a reputable organization or individual. Avoid scanning QR codes from unknown or untrusted sources, as they may lead to phishing websites or initiate unwanted transactions.
5. Malware and Keyloggers
In some cases, phishers may use malware or keyloggers to steal sensitive information from their victims’ computers or mobile devices. Malware is malicious software that can be installed on a device without the user’s knowledge, while keyloggers record every keystroke entered by the user.
To protect yourself from malware and keyloggers, keep your operating system and software up to date, install a reputable antivirus program, and avoid downloading files or clicking on links from unknown or untrusted sources.
6. Impersonation of Customer Support
Phishers may also impersonate customer support representatives from cryptocurrency exchanges or wallet providers to gain access to victims’ accounts. They may contact victims via email, phone, or social media, claiming to need their login credentials or private keys to resolve an issue or verify their identity.
Never share your login credentials, private keys, or seed phrases with anyone, including customer support representatives. Legitimate customer support will never ask for this information. If you are contacted by someone claiming to be customer support, verify their identity by contacting the organization directly through their official website or channels.
Protecting Yourself from Crypto Phishing
Now that you have a better understanding of how phishing scams work in the crypto space, let’s explore some practical steps you can take to protect yourself from these attacks.
1. Be Vigilant and Skeptical
The most important defense against phishing scams is to be vigilant and skeptical of any unsolicited messages, emails, or requests for personal information. Always double-check the sender’s address, the URL of the website you are visiting, and the legitimacy of social media profiles.
2. Enable Two-Factor Authentication (2FA)
Two-factor authentication (2FA) adds an extra layer of security to your accounts by requiring you to enter a code from your phone or another device in addition to your password. This makes it much more difficult for phishers to access your accounts, even if they manage to steal your password.
3. Use a Hardware Wallet
A hardware wallet is a physical device that stores your private keys offline, making them inaccessible to hackers. When you want to make a transaction, you need to connect the hardware wallet to your computer or mobile device and authorize the transaction manually. This significantly reduces the risk of phishing attacks, as your private keys are never exposed to the internet.
4. Keep Your Software Up to Date
Keeping your operating system, software, and antivirus program up to date is crucial for protecting yourself from malware and keyloggers. Software updates often include security patches that fix vulnerabilities that could be exploited by hackers.
5. Educate Yourself
Stay informed about the latest phishing tactics and techniques by reading articles, attending webinars, and following reputable sources of information in the crypto community. The more you know about phishing scams, the better equipped you will be to recognize and avoid them.
6. Report Phishing Attempts
If you encounter a phishing attempt, report it to the relevant organization or platform. This will help them to take action against the phisher and prevent others from falling victim to the scam.
Conclusion
Phishing scams pose a significant threat to cryptocurrency users, but by understanding how these attacks work and taking proactive steps to protect yourself, you can significantly reduce your risk of falling victim. Remember to be vigilant, skeptical, and always double-check the legitimacy of any messages, emails, or requests for personal information. By following the tips outlined in this article, you can safeguard your digital assets and enjoy the benefits of the crypto world with greater peace of mind.

