“How Blockchain Enhances Cybersecurity: A Deep Dive
Related Articles How Blockchain Enhances Cybersecurity: A Deep Dive
- Starbucks: A Global Coffeehouse Phenomenon
- REKOMENDASI HOSTING BAYAR BULANAN MURAH BERKUALITAS
- Green Cloud Data Centers
- Bitcoin Halving 2024
- How the Stock Market Work in Your Country?
Introduction
We will be happy to explore interesting topics related to How Blockchain Enhances Cybersecurity: A Deep Dive. Come on knit interesting information and provide new insights to readers.
Table of Content
How Blockchain Enhances Cybersecurity: A Deep Dive

In an era defined by escalating cyber threats and data breaches, the need for robust and innovative cybersecurity solutions has never been more critical. While traditional security measures have proven inadequate in the face of sophisticated attacks, blockchain technology has emerged as a promising tool to fortify digital defenses. Blockchain, originally conceived as the backbone of cryptocurrencies like Bitcoin, possesses inherent characteristics that can significantly enhance cybersecurity across various domains. This article delves into the mechanisms by which blockchain strengthens cybersecurity, highlighting its advantages, applications, and potential limitations.
Understanding Blockchain: The Foundation of Enhanced Security
Before exploring the cybersecurity benefits of blockchain, it’s essential to understand its fundamental principles:
-
Decentralization: Unlike traditional centralized systems where data is stored in a single location, blockchain distributes data across a network of computers (nodes). This decentralization eliminates single points of failure, making it extremely difficult for attackers to compromise the entire system.
-
Immutability: Once data is recorded on a blockchain, it cannot be altered or deleted. Each block of data is cryptographically linked to the previous block, creating an unchangeable chain of records. This immutability ensures the integrity and authenticity of data.
-
Transparency: All transactions on a public blockchain are visible to all participants. While the identities of users may be pseudonymous, the transaction history is transparent, allowing for auditing and verification.
-
Cryptography: Blockchain relies heavily on cryptography to secure data and transactions. Cryptographic hash functions and digital signatures ensure that data is tamper-proof and that transactions are authorized.
-
Consensus Mechanisms: Blockchain networks employ consensus mechanisms to validate transactions and ensure that all nodes agree on the state of the ledger. These mechanisms, such as Proof-of-Work (PoW) or Proof-of-Stake (PoS), prevent malicious actors from manipulating the blockchain.
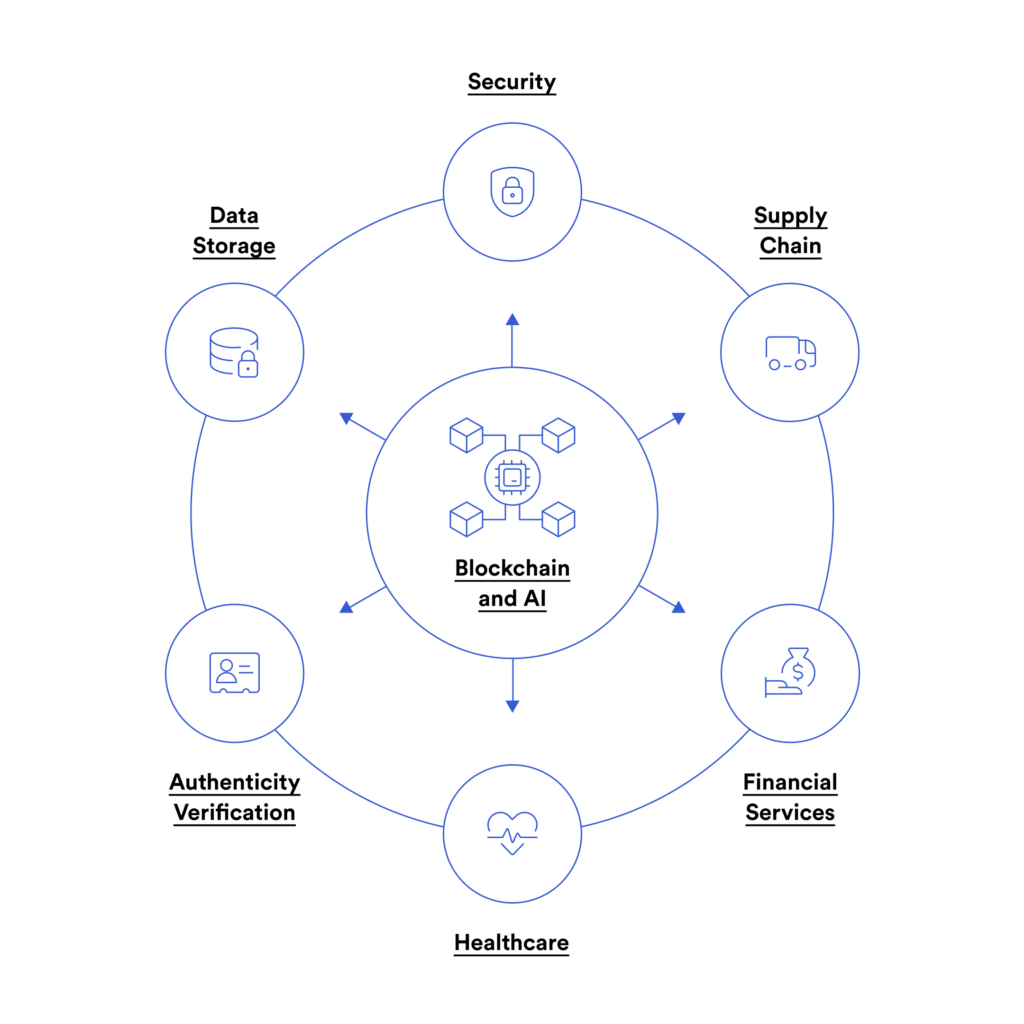
Blockchain’s Role in Enhancing Cybersecurity
-
Data Integrity and Tamper Resistance:
- Immutable Records: Blockchain’s immutability ensures that data stored on the chain cannot be altered without detection. This is crucial for maintaining the integrity of sensitive information, such as medical records, financial transactions, and supply chain data.
- Audit Trails: The transparent and chronological nature of blockchain creates an auditable trail of all transactions and data changes. This allows for easy tracking of data provenance and identification of any unauthorized modifications.
- Data Verification: Cryptographic hash functions ensure that data remains unchanged. Any attempt to tamper with the data will result in a different hash value, immediately alerting users to the alteration.
-
Identity and Access Management:
- Decentralized Identity: Blockchain can be used to create decentralized identity systems, where users control their own digital identities without relying on central authorities. This reduces the risk of identity theft and fraud.
- Secure Authentication: Blockchain-based authentication systems can replace traditional password-based logins with more secure methods, such as multi-factor authentication using cryptographic keys.
- Access Control: Blockchain can enforce granular access control policies, ensuring that only authorized users can access specific data or resources. Smart contracts can automate access control based on predefined rules.
-
Supply Chain Security:
- Tracking and Tracing: Blockchain enables end-to-end tracking and tracing of products throughout the supply chain. This helps prevent counterfeiting, ensures product authenticity, and improves supply chain transparency.
- Provenance Verification: Consumers can use blockchain to verify the origin and history of products, ensuring that they are genuine and ethically sourced.
- Supply Chain Integrity: By providing a tamper-proof record of all transactions and data related to a product, blockchain enhances the integrity of the supply chain and reduces the risk of fraud.
-
Secure Data Sharing:
- Controlled Data Access: Blockchain allows data owners to control who has access to their data and for how long. Smart contracts can automate data sharing agreements and enforce data privacy policies.
- Data Monetization: Blockchain enables individuals and organizations to monetize their data by securely sharing it with others in exchange for compensation.
- Data Privacy: Blockchain-based data sharing solutions can incorporate privacy-enhancing technologies, such as zero-knowledge proofs and homomorphic encryption, to protect sensitive data while allowing for analysis and collaboration.
-
IoT Security:
- Device Authentication: Blockchain can be used to securely authenticate IoT devices and prevent unauthorized access. Each device can have a unique digital identity stored on the blockchain.
- Data Integrity: Blockchain ensures the integrity of data generated by IoT devices, preventing tampering and ensuring that the data is reliable.
- Secure Communication: Blockchain can facilitate secure communication between IoT devices, protecting against eavesdropping and man-in-the-middle attacks.
-
Protection Against DDoS Attacks:
- Distributed Architecture: Blockchain’s decentralized nature makes it more resilient to DDoS attacks. Since there is no central server to target, attackers must overwhelm the entire network, which is a much more difficult task.
- Traffic Filtering: Blockchain-based solutions can be used to filter malicious traffic and prevent it from reaching critical systems.
- Reputation Systems: Blockchain can be used to build reputation systems that identify and penalize malicious actors, making it more difficult for them to launch DDoS attacks.
Use Cases of Blockchain in Cybersecurity
-
Healthcare:
- Secure Medical Records: Blockchain can be used to store and manage medical records securely, ensuring that only authorized personnel can access patient data.
- Drug Supply Chain: Blockchain can track the movement of drugs throughout the supply chain, preventing counterfeiting and ensuring that patients receive genuine medications.
- Clinical Trial Data: Blockchain can be used to securely store and manage clinical trial data, ensuring the integrity and accuracy of research findings.
-
Finance:
- Secure Transactions: Blockchain can be used to process financial transactions securely, reducing the risk of fraud and ensuring that payments are processed accurately.
- Identity Verification: Blockchain can be used to verify the identities of customers, reducing the risk of identity theft and fraud.
- Regulatory Compliance: Blockchain can help financial institutions comply with regulatory requirements, such as KYC and AML.
-
Government:
- Secure Voting: Blockchain can be used to conduct secure and transparent elections, preventing voter fraud and ensuring that all votes are accurately counted.
- Land Registry: Blockchain can be used to create a secure and immutable record of land ownership, reducing the risk of property disputes and fraud.
- Digital Identity: Blockchain can be used to create a secure and portable digital identity for citizens, making it easier to access government services.
Challenges and Limitations of Blockchain in Cybersecurity
While blockchain offers numerous benefits for cybersecurity, it also has some limitations:
- Scalability: Blockchain networks can be slow and inefficient, especially when processing large volumes of transactions. This can limit their applicability in certain cybersecurity scenarios.
- Complexity: Implementing and managing blockchain-based cybersecurity solutions can be complex and require specialized expertise.
- Regulatory Uncertainty: The regulatory landscape for blockchain is still evolving, which can create uncertainty for organizations considering adopting the technology.
- Key Management: Securing cryptographic keys is critical for maintaining the security of blockchain-based systems. If keys are lost or stolen, data can be compromised.
- Quantum Computing: The advent of quantum computing poses a potential threat to blockchain security, as quantum computers could potentially break the cryptographic algorithms used to secure blockchain networks.
Conclusion
Blockchain technology holds immense potential for enhancing cybersecurity across various industries and applications. Its decentralized, immutable, and transparent nature provides a strong foundation for building more secure and resilient systems. By leveraging blockchain, organizations can improve data integrity, strengthen identity and access management, secure supply chains, enable secure data sharing, and protect against DDoS attacks.
While challenges and limitations exist, ongoing research and development efforts are addressing these issues. As blockchain technology matures and becomes more widely adopted, it is poised to play an increasingly important role in the fight against cybercrime and the protection of digital assets. By understanding the capabilities and limitations of blockchain, organizations can strategically leverage this technology to bolster their cybersecurity defenses and create a more secure digital world.