“Hardware Wallets: The Gold Standard for Cryptocurrency Security
Related Articles Hardware Wallets: The Gold Standard for Cryptocurrency Security
- Multi-cloud Data Services
- Uniswap: A Deep Dive Into Decentralized Exchange
- How Many Ounces In A Gallon? A Comprehensive Guide
- The Enduring Appeal Of Snake: A Journey Through A Pixelated Phenomenon
- car insurance zenith
Introduction
On this special occasion, we are happy to review interesting topics related to Hardware Wallets: The Gold Standard for Cryptocurrency Security. Let’s knit interesting information and provide new insights to readers.
Table of Content
Hardware Wallets: The Gold Standard for Cryptocurrency Security

In the dynamic world of cryptocurrencies, security is of utmost importance. As digital assets gain popularity, they become increasingly attractive targets for malicious actors. Protecting your cryptocurrency holdings requires implementing robust security measures, and hardware wallets have emerged as a leading solution for secure storage and management of digital assets.
What is a Hardware Wallet?
A hardware wallet is a physical electronic device specifically designed to securely store a user’s private keys offline. Private keys are essential for accessing and managing cryptocurrencies, as they authorize transactions and grant ownership of digital assets. Unlike software wallets, which store private keys on a computer or smartphone, hardware wallets keep private keys isolated from internet-connected devices, significantly reducing the risk of online attacks.
Hardware wallets typically resemble small USB drives or compact devices with a screen and buttons. They are compatible with various cryptocurrencies and can be connected to a computer or mobile device to manage and transact with digital assets.
How Does a Hardware Wallet Work?
Hardware wallets operate on a simple yet effective principle: keep private keys offline and secure. When you set up a hardware wallet, it generates a unique private key and stores it securely within the device. The private key never leaves the hardware wallet, ensuring it remains protected from potential threats.
To conduct a transaction, you connect the hardware wallet to your computer or mobile device and use a compatible wallet interface. The transaction details are displayed on the hardware wallet’s screen, allowing you to verify the information before approving the transaction. Once you confirm the transaction, the hardware wallet uses its private key to digitally sign the transaction, which is then broadcast to the cryptocurrency network.
Because the private key remains securely stored within the hardware wallet, even if your computer or mobile device is compromised, your cryptocurrency holdings remain safe.
Benefits of Using a Hardware Wallet
Hardware wallets offer several advantages over other types of cryptocurrency wallets, making them a preferred choice for security-conscious cryptocurrency users:
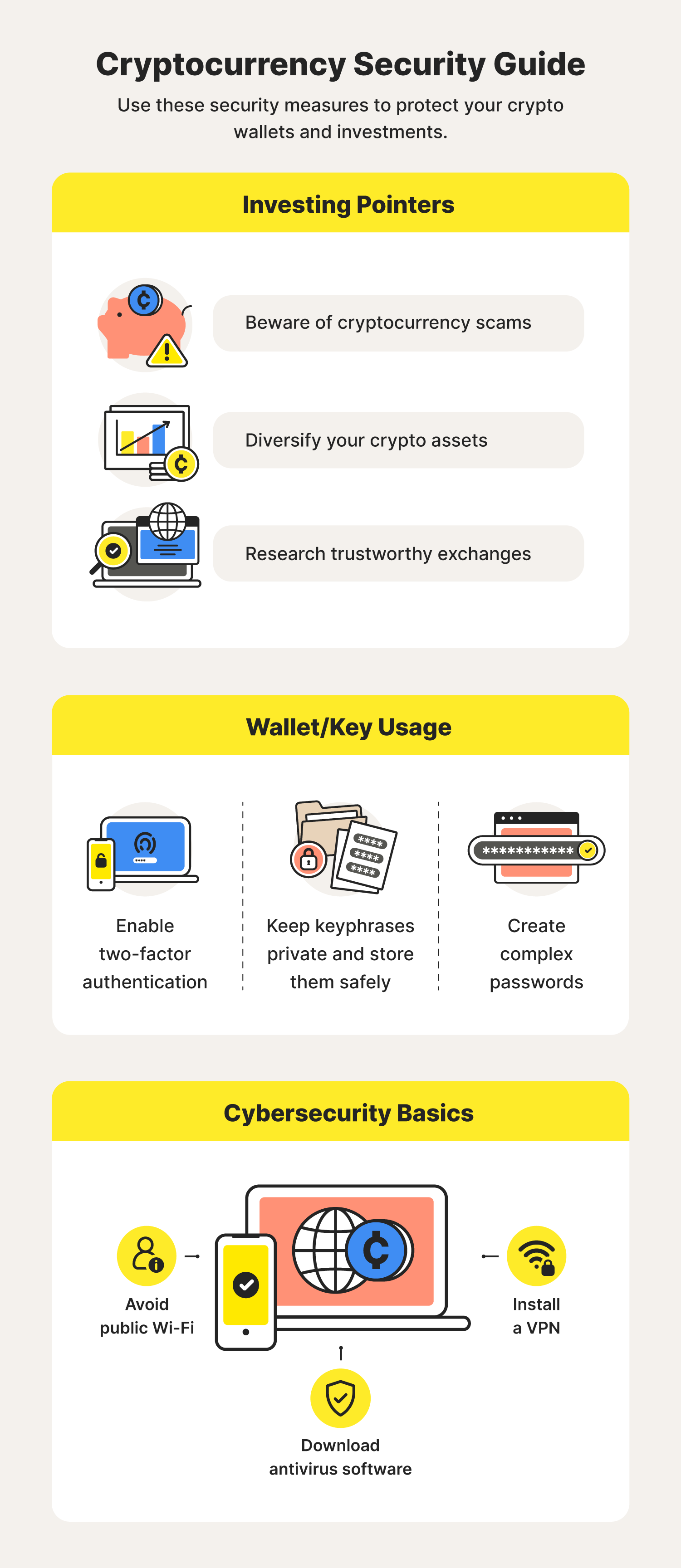
- Enhanced Security: Hardware wallets provide the highest level of security for cryptocurrency storage. By keeping private keys offline, they eliminate the risk of online attacks such as malware, phishing scams, and keyloggers.
- Offline Storage: Private keys are stored offline within the hardware wallet, ensuring they are not exposed to the internet or vulnerable to remote attacks.
- Transaction Verification: Hardware wallets display transaction details on their screen, allowing you to verify the information before approving the transaction. This prevents unauthorized transactions and protects against man-in-the-middle attacks.
- Multi-Currency Support: Most hardware wallets support a wide range of cryptocurrencies, allowing you to manage multiple digital assets in one secure device.
- User-Friendly Interface: Hardware wallets are designed to be user-friendly, with intuitive interfaces that make it easy to manage and transact with cryptocurrencies.
- Backup and Recovery: Hardware wallets provide backup and recovery options, allowing you to restore your wallet and access your funds in case of loss or damage.
- Tamper-Proof Design: Hardware wallets are designed to be tamper-proof, with physical security measures that prevent unauthorized access to the device and its contents.
Popular Hardware Wallet Brands
Several reputable hardware wallet brands offer secure and reliable solutions for cryptocurrency storage. Some of the most popular hardware wallet brands include:
- Ledger: Ledger is a leading hardware wallet manufacturer known for its secure and user-friendly devices. Ledger wallets support a wide range of cryptocurrencies and offer advanced security features.
- Trezor: Trezor is another popular hardware wallet brand that offers secure and reliable cryptocurrency storage. Trezor wallets are known for their open-source design and strong security features.
- Coldcard: Coldcard is a hardware wallet designed for advanced users who prioritize security and privacy. Coldcard wallets offer advanced features such as air-gapped operation and support for multi-signature setups.
- KeepKey: KeepKey is a hardware wallet that offers a sleek and user-friendly design. KeepKey wallets support a variety of cryptocurrencies and offer a simple and secure way to manage digital assets.
How to Choose a Hardware Wallet
Choosing the right hardware wallet depends on your individual needs and preferences. Consider the following factors when selecting a hardware wallet:
- Cryptocurrency Support: Ensure the hardware wallet supports the cryptocurrencies you want to store.
- Security Features: Look for hardware wallets with strong security features, such as secure element chips, tamper-proof design, and open-source firmware.
- User Interface: Choose a hardware wallet with a user-friendly interface that is easy to navigate and understand.
- Backup and Recovery: Ensure the hardware wallet provides backup and recovery options, allowing you to restore your wallet in case of loss or damage.
- Price: Hardware wallets vary in price, so consider your budget when making a selection.
Setting Up a Hardware Wallet
Setting up a hardware wallet is a straightforward process that typically involves the following steps:
- Purchase a Hardware Wallet: Buy a hardware wallet from a reputable vendor or directly from the manufacturer’s website.
- Install the Wallet Software: Download and install the wallet software provided by the hardware wallet manufacturer on your computer or mobile device.
- Connect the Hardware Wallet: Connect the hardware wallet to your computer or mobile device using a USB cable.
- Initialize the Hardware Wallet: Follow the instructions provided by the wallet software to initialize the hardware wallet and create a new wallet.
- Write Down the Recovery Seed: The hardware wallet will generate a recovery seed, which is a list of 12 or 24 words. Write down the recovery seed on a piece of paper and store it in a safe and secure location.
- Verify the Recovery Seed: Some hardware wallets will prompt you to verify the recovery seed to ensure you have written it down correctly.
- Set a PIN Code: Set a PIN code for your hardware wallet to protect it from unauthorized access.
- Start Using the Hardware Wallet: Once the setup process is complete, you can start using the hardware wallet to manage and transact with your cryptocurrencies.
Tips for Using a Hardware Wallet Safely
To ensure the security of your cryptocurrency holdings, follow these tips when using a hardware wallet:
- Buy from Reputable Sources: Purchase your hardware wallet from a reputable vendor or directly from the manufacturer’s website. Avoid buying hardware wallets from third-party sellers or online marketplaces, as they may be tampered with.
- Keep Your Recovery Seed Safe: Store your recovery seed in a safe and secure location, away from prying eyes. Do not store your recovery seed on your computer or mobile device.
- Use a Strong PIN Code: Set a strong PIN code for your hardware wallet to protect it from unauthorized access.
- Update Firmware Regularly: Keep your hardware wallet’s firmware up to date to ensure you have the latest security features and bug fixes.
- Verify Transaction Details: Always verify transaction details on the hardware wallet’s screen before approving the transaction.
- Protect Your Computer and Mobile Device: Keep your computer and mobile device secure by installing antivirus software and avoiding suspicious websites and links.
- Be Aware of Phishing Scams: Be aware of phishing scams that attempt to trick you into revealing your private keys or recovery seed. Never share your private keys or recovery seed with anyone.
Conclusion
Hardware wallets are an essential tool for securing your cryptocurrency holdings. By keeping private keys offline and providing a secure environment for transaction signing, hardware wallets offer the highest level of security against online attacks. Whether you are a seasoned cryptocurrency investor or just starting out, investing in a hardware wallet is a wise decision to protect your digital assets and ensure peace of mind.