“Decentralized Identity (DID): A Paradigm Shift in Digital Trust
Related Articles Decentralized Identity (DID): A Paradigm Shift in Digital Trust
- Blockchain Technology: A Comprehensive Overview
- How to Buy Life Insurance
- forex4money
- which car insurance is cheaper
- Atlassian Cloud Vs Data Center
Introduction
We will be happy to explore interesting topics related to Decentralized Identity (DID): A Paradigm Shift in Digital Trust. Come on knit interesting information and provide new insights to readers.
Table of Content
Decentralized Identity (DID): A Paradigm Shift in Digital Trust
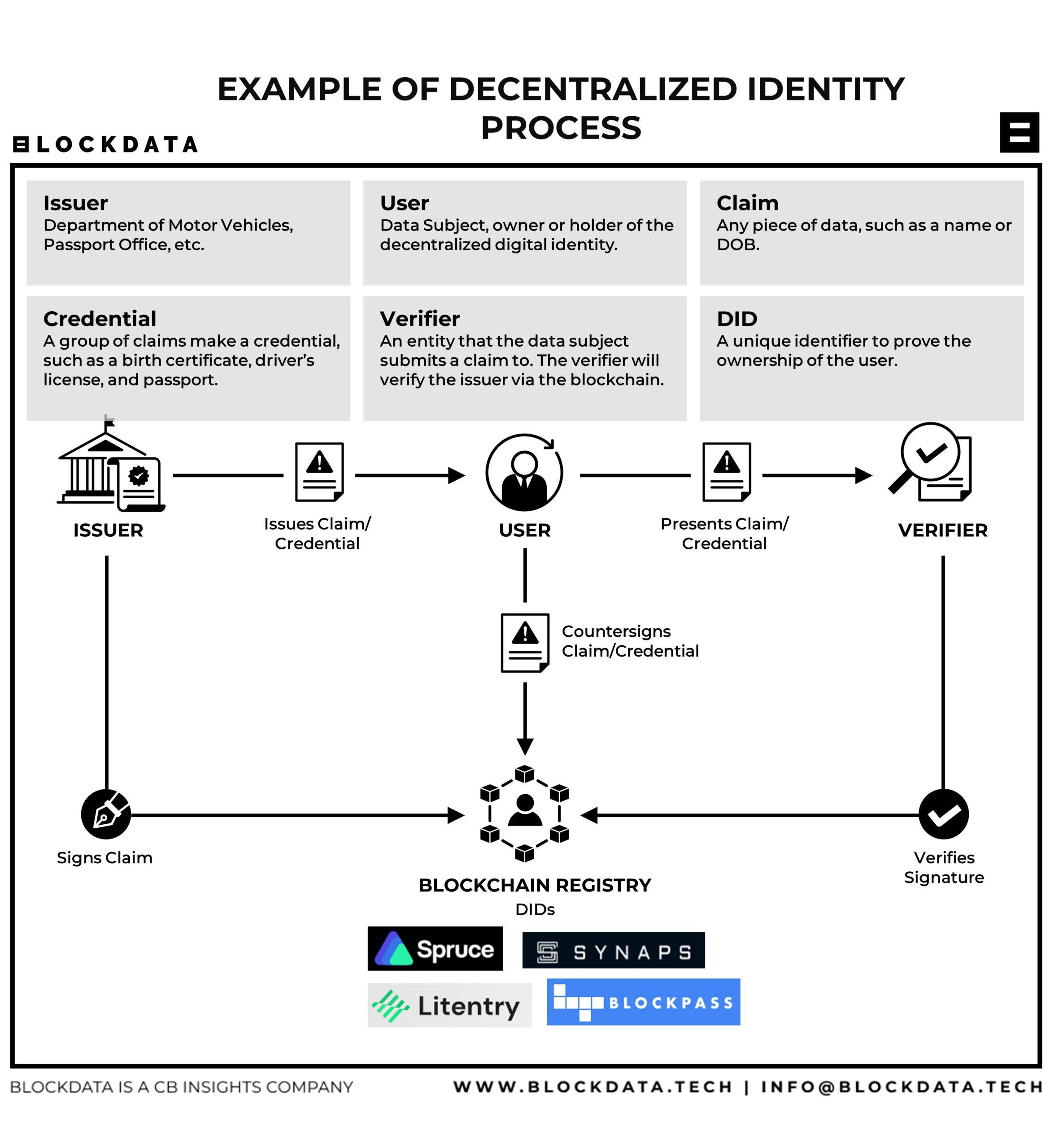
In an increasingly interconnected and digital-centric world, the concept of identity has undergone a profound transformation. Traditional identity management systems, reliant on centralized authorities, have proven vulnerable to data breaches, privacy violations, and a lack of user control. Decentralized Identity (DID) emerges as a revolutionary approach, promising to reshape how we establish, manage, and protect our digital identities.
The Limitations of Centralized Identity Systems
For decades, our digital identities have been governed by centralized entities such as governments, corporations, and social media platforms. These systems operate on a model where users entrust their personal information to these organizations, who then act as custodians of that data. While seemingly convenient, this approach carries significant risks:
- Data Breaches: Centralized databases are prime targets for cyberattacks. A single breach can expose the personal information of millions of users, leading to identity theft, financial losses, and reputational damage.
- Privacy Violations: Centralized entities often collect and analyze user data for various purposes, including targeted advertising and profiling. This raises serious concerns about privacy and the potential for misuse of personal information.
- Lack of User Control: Users have limited control over their data in centralized systems. They are often forced to accept lengthy terms of service and privacy policies, with little say in how their information is used.
- Single Points of Failure: Centralized systems are vulnerable to outages and disruptions. If a central authority fails, users may lose access to their digital identities and the services associated with them.
- Identity Silos: Different platforms and services often require users to create separate accounts and manage multiple sets of credentials. This creates identity silos, making it difficult to seamlessly interact across different online environments.
Enter Decentralized Identity (DID)
Decentralized Identity (DID) offers a paradigm shift in how we manage our digital identities. It empowers individuals to create and control their own identities, without relying on centralized authorities. DID is based on the principles of decentralization, privacy, and user autonomy.
Key Concepts of Decentralized Identity
-
Decentralized Identifiers (DIDs): DIDs are unique, globally resolvable identifiers that are not controlled by any single entity. They are typically generated using cryptographic keys and stored on distributed ledgers or decentralized networks.
-
DID Documents: A DID document contains metadata associated with a DID, including public keys, service endpoints, and other relevant information. This document enables others to verify the identity of the DID controller and interact with them securely.
-
Verifiable Credentials: Verifiable credentials are digital credentials that are issued by trusted entities and can be cryptographically verified. They allow individuals to prove specific claims about themselves without revealing unnecessary personal information.
-
Decentralized Key Management: DID relies on decentralized key management, where users control their own cryptographic keys. This gives them complete control over their identities and the ability to authorize transactions and interactions.
How Decentralized Identity Works
-
DID Creation: A user generates a DID using a DID method, which specifies how the DID is created and managed. The DID is typically stored on a distributed ledger or decentralized network.
-
DID Document Publication: The user publishes a DID document that contains information about their identity, such as public keys and service endpoints. This document allows others to verify the user’s identity and interact with them securely.
-
Verifiable Credential Issuance: A trusted entity issues a verifiable credential to the user, attesting to a specific claim about them. The credential is cryptographically signed by the issuer.
-
Verifiable Credential Presentation: When the user needs to prove a claim, they present the verifiable credential to a verifier. The verifier can verify the authenticity and validity of the credential using the issuer’s public key.
-
Secure Interaction: Using the DID document and verifiable credentials, the user can securely interact with other parties, such as websites, applications, and services.
Benefits of Decentralized Identity
- Enhanced Security: DID reduces the risk of data breaches by eliminating the need for centralized databases. Users control their own data and can selectively share information with trusted parties.
- Improved Privacy: DID empowers users to control their personal information and minimize the amount of data they share. Verifiable credentials allow users to prove specific claims without revealing unnecessary details.
- User Autonomy: DID gives users complete control over their digital identities. They can create, manage, and revoke their identities without relying on centralized authorities.
- Interoperability: DID promotes interoperability across different platforms and services. Users can use the same identity to access multiple online environments, eliminating the need for separate accounts and credentials.
- Reduced Identity Theft: DID makes it more difficult for fraudsters to steal and misuse identities. Cryptographic keys and verifiable credentials provide strong authentication and verification mechanisms.
- Self-Sovereign Identity: DID enables self-sovereign identity, where individuals have complete control over their digital identities and can interact with the world on their own terms.
Use Cases of Decentralized Identity
DID has a wide range of potential use cases across various industries and sectors:
- Healthcare: Patients can use DID to control their medical records and share them securely with healthcare providers.
- Finance: Individuals can use DID to verify their identity for financial transactions and access banking services.
- Education: Students can use DID to manage their academic credentials and transcripts.
- Supply Chain: DID can be used to track and verify the provenance of goods and materials throughout the supply chain.
- Government: Governments can use DID to issue digital IDs and provide citizens with access to government services.
- Social Media: Users can use DID to control their social media identities and protect their privacy.
- Internet of Things (IoT): DID can be used to authenticate and authorize devices in IoT networks.
Challenges and Considerations
While DID offers numerous benefits, there are also challenges and considerations that need to be addressed:
- Scalability: Decentralized networks need to be scalable to handle the increasing number of DIDs and transactions.
- Usability: DID systems need to be user-friendly and accessible to a wide range of users.
- Security: DID systems need to be secure and resistant to attacks, such as key compromise and identity theft.
- Regulation: Clear and consistent regulations are needed to govern the use of DID and protect user rights.
- Interoperability: Different DID methods and implementations need to be interoperable to ensure seamless integration across different platforms and services.
- Key Management: Secure key management is crucial for protecting DID identities. Users need to be educated on how to properly store and manage their cryptographic keys.
- Recovery Mechanisms: Mechanisms are needed to recover DIDs in case of key loss or compromise.
- Trust Models: Establishing trust models for verifiable credential issuers is essential for ensuring the credibility of DID systems.
The Future of Decentralized Identity
Decentralized Identity is still in its early stages of development, but it has the potential to revolutionize how we manage our digital identities. As the technology matures and adoption increases, we can expect to see DID become an integral part of our digital lives.
Key Trends Shaping the Future of DID:
- Standardization: Efforts are underway to standardize DID methods and protocols to ensure interoperability and compatibility.
- Wallet Integration: DID wallets are becoming more sophisticated and user-friendly, making it easier for users to manage their identities and credentials.
- Enterprise Adoption: Businesses are increasingly exploring DID as a way to improve security, privacy, and customer experience.
- Government Initiatives: Governments are launching pilot projects to explore the use of DID for digital IDs and citizen services.
- Integration with Blockchain: DID is often integrated with blockchain technology to provide a secure and transparent infrastructure for identity management.
- Focus on User Experience: Developers are focusing on improving the user experience of DID systems to make them more accessible and intuitive.
- Collaboration and Partnerships: Collaboration between industry stakeholders, governments, and standards organizations is essential for driving the adoption of DID.
Conclusion
Decentralized Identity represents a fundamental shift in the way we approach digital identity management. By empowering individuals to control their own identities, DID offers a more secure, private, and user-centric alternative to traditional centralized systems. While challenges remain, the potential benefits of DID are significant, and its adoption is likely to grow in the coming years. As we navigate the increasingly complex digital landscape, DID promises to play a crucial role in establishing trust, protecting privacy, and enabling seamless interactions across the digital world.

