“Cryptographic Hash Functions: A Cornerstone of Modern Security
Related Articles Cryptographic Hash Functions: A Cornerstone of Modern Security
- car insurance hong kong
- forex4money
- car insurance yearly cost
- Decentralized Autonomous Organizations (DAOs): A Deep Dive Into The Future Of Governance
- Tokenomics: The Engine Driving Cryptocurrency Value
Introduction
On this special occasion, we are happy to review interesting topics related to Cryptographic Hash Functions: A Cornerstone of Modern Security. Come on knit interesting information and provide new insights to readers.
Table of Content
Cryptographic Hash Functions: A Cornerstone of Modern Security
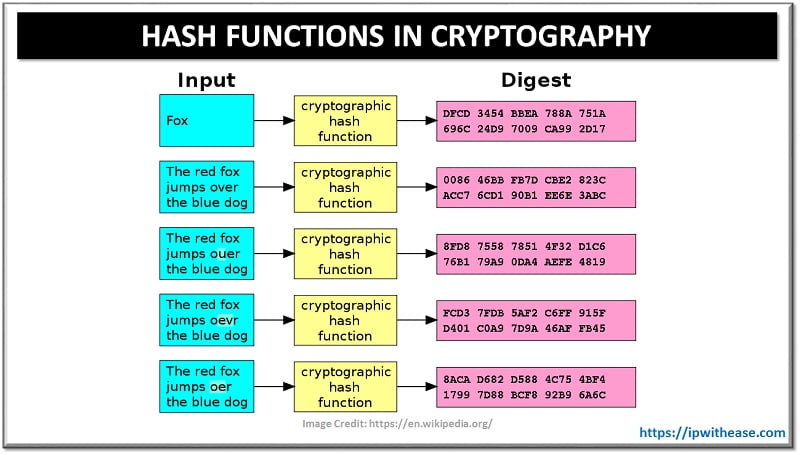
In the digital age, where information reigns supreme, ensuring the integrity and authenticity of data is paramount. Cryptographic hash functions serve as a fundamental building block in achieving these security goals. These mathematical algorithms transform data of any size into a fixed-size "fingerprint," known as a hash value or digest. This seemingly simple process underpins a wide array of security applications, from password storage to digital signatures and blockchain technology.
Understanding the Basics
At its core, a cryptographic hash function takes an input message (which can be a file, a piece of text, or any digital data) and produces a fixed-size output, the hash value. This process is deterministic, meaning that the same input will always produce the same hash value. However, even a tiny change in the input message will result in a drastically different hash value.
Key Properties of Cryptographic Hash Functions
To be considered cryptographically secure, a hash function must possess several crucial properties:
-
Pre-image Resistance (One-Way Property): Given a hash value, it should be computationally infeasible to find the original input message that produced that hash. This property is essential for protecting passwords, where the hash of the password is stored instead of the password itself.
-
Second Pre-image Resistance (Weak Collision Resistance): Given an input message and its hash value, it should be computationally infeasible to find a different input message that produces the same hash value. This property prevents an attacker from substituting a malicious message for a legitimate one.
-
Collision Resistance (Strong Collision Resistance): It should be computationally infeasible to find any two different input messages that produce the same hash value. This is the strongest security requirement, as it protects against any form of message substitution or forgery.
-
Deterministic: For a given input, the hash function always produces the same output. This is critical for verifying data integrity, as any change to the input will result in a different hash value.
-
Efficiency: The hash function should be computationally efficient, meaning it can quickly generate hash values for large amounts of data. This is important for practical applications where performance is a concern.
How Cryptographic Hash Functions Work
While the specific algorithms vary, most cryptographic hash functions follow a general structure:
-
Padding: The input message is padded to ensure its length is a multiple of a specific block size. This padding process is deterministic and reversible.
-
Parsing: The padded message is divided into fixed-size blocks.
-
Initialization: An initial hash value (IV) is set. This IV is a constant value specific to the hash function.
-
Compression Function: The core of the hash function is the compression function, which takes the previous hash value and a message block as input and produces a new hash value. This compression function is applied iteratively to each message block.
-
Finalization: After processing all message blocks, a finalization step may be performed to mix the final hash value and produce the output hash value.
Examples of Cryptographic Hash Functions
Several cryptographic hash functions have been developed over the years, each with its own strengths and weaknesses. Some of the most widely used include:
-
MD5 (Message Digest 5): An older hash function that produces a 128-bit hash value. While it was once widely used, MD5 is now considered cryptographically broken due to the discovery of collision attacks. It should not be used for security-critical applications.
-
SHA-1 (Secure Hash Algorithm 1): Another older hash function that produces a 160-bit hash value. Like MD5, SHA-1 has been found to be vulnerable to collision attacks, although the attacks are more complex. It is also being phased out in favor of more secure alternatives.
-
SHA-2 (Secure Hash Algorithm 2): A family of hash functions that includes SHA-224, SHA-256, SHA-384, and SHA-512, which produce hash values of 224, 256, 384, and 512 bits, respectively. SHA-2 is considered more secure than MD5 and SHA-1 and is widely used in various security applications.
-
SHA-3 (Secure Hash Algorithm 3): The latest generation of SHA hash functions, selected through a public competition. SHA-3 is based on a different design principle than SHA-1 and SHA-2, making it more resistant to certain types of attacks. It offers various output sizes, including 224, 256, 384, and 512 bits.
-
BLAKE2: A fast and secure hash function that is often used as an alternative to SHA-3. It is known for its high performance and resistance to various attacks.
Applications of Cryptographic Hash Functions
Cryptographic hash functions have a wide range of applications in computer security and beyond:
-
Password Storage: Instead of storing passwords in plain text, websites and applications store the hash of the password. When a user tries to log in, the hash of the entered password is compared to the stored hash. If they match, the user is authenticated without ever revealing the actual password.
-
Data Integrity Verification: Hash functions can be used to verify the integrity of data during transmission or storage. By calculating the hash of a file before sending it and comparing it to the hash calculated after receiving it, any tampering or corruption can be detected.
-
Digital Signatures: Hash functions are used in digital signatures to create a "fingerprint" of a document or message. This fingerprint is then encrypted with the sender’s private key, creating a digital signature. The recipient can verify the signature by decrypting it with the sender’s public key and comparing the resulting hash with the hash of the received document.
-
Message Authentication Codes (MACs): MACs use hash functions to generate a tag that authenticates the message’s origin and ensures its integrity. A secret key is used in conjunction with the hash function to create the MAC, preventing unauthorized parties from forging or altering the message.
-
Blockchain Technology: Cryptographic hash functions are a cornerstone of blockchain technology. They are used to link blocks of transactions together in a chain, creating a tamper-proof record of all transactions. The hash of each block includes the hash of the previous block, making it impossible to alter any block without invalidating all subsequent blocks.
-
Data Deduplication: Hash functions can be used to identify duplicate files or data blocks, allowing for efficient storage and bandwidth utilization. By calculating the hash of each file or block, duplicates can be easily identified and eliminated.
The Importance of Choosing the Right Hash Function
Selecting the appropriate cryptographic hash function is crucial for ensuring the security of your applications. It’s essential to choose a hash function that is considered cryptographically secure and has not been found to be vulnerable to attacks. Avoid using outdated or broken hash functions like MD5 or SHA-1.
Consider the following factors when choosing a hash function:
- Security Requirements: Determine the level of security required for your application. If you need the highest level of security, choose a hash function with a longer output length and a strong security reputation.
- Performance Requirements: Consider the performance requirements of your application. Some hash functions are faster than others, so choose one that meets your performance needs without compromising security.
- Standardization: Choose a hash function that is widely accepted and standardized. This will ensure that your application is compatible with other systems and that the hash function is well-supported.
The Future of Cryptographic Hash Functions
As technology evolves, the need for secure cryptographic hash functions will only continue to grow. Researchers are constantly working to develop new and improved hash functions that are resistant to emerging threats. Quantum computing, in particular, poses a significant challenge to existing cryptographic algorithms, including hash functions. Post-quantum cryptography research is focused on developing algorithms that are resistant to attacks from both classical and quantum computers.
Conclusion
Cryptographic hash functions are essential tools for ensuring data integrity, authentication, and security in a wide range of applications. By understanding the properties of these functions and choosing the right one for your needs, you can build more secure and reliable systems. As technology continues to advance, it’s crucial to stay informed about the latest developments in cryptographic hash functions and adapt your security practices accordingly.


1 comment