“Crypto Crime Trends in 2025: A Landscape of Innovation and Evasion
Related Articles Crypto Crime Trends in 2025: A Landscape of Innovation and Evasion
- Block Reward: The Backbone Of Cryptocurrency Mining
- Cloud Data Computing
- Legal Tender: Understanding Its Role And Significance In Monetary Systems
- Private Keys: The Cornerstone Of Digital Security
- The United States Postal Service: An American Institution At A Crossroads
Introduction
We will be happy to explore interesting topics related to Crypto Crime Trends in 2025: A Landscape of Innovation and Evasion. Come on knit interesting information and provide new insights to readers.
Table of Content
Crypto Crime Trends in 2025: A Landscape of Innovation and Evasion
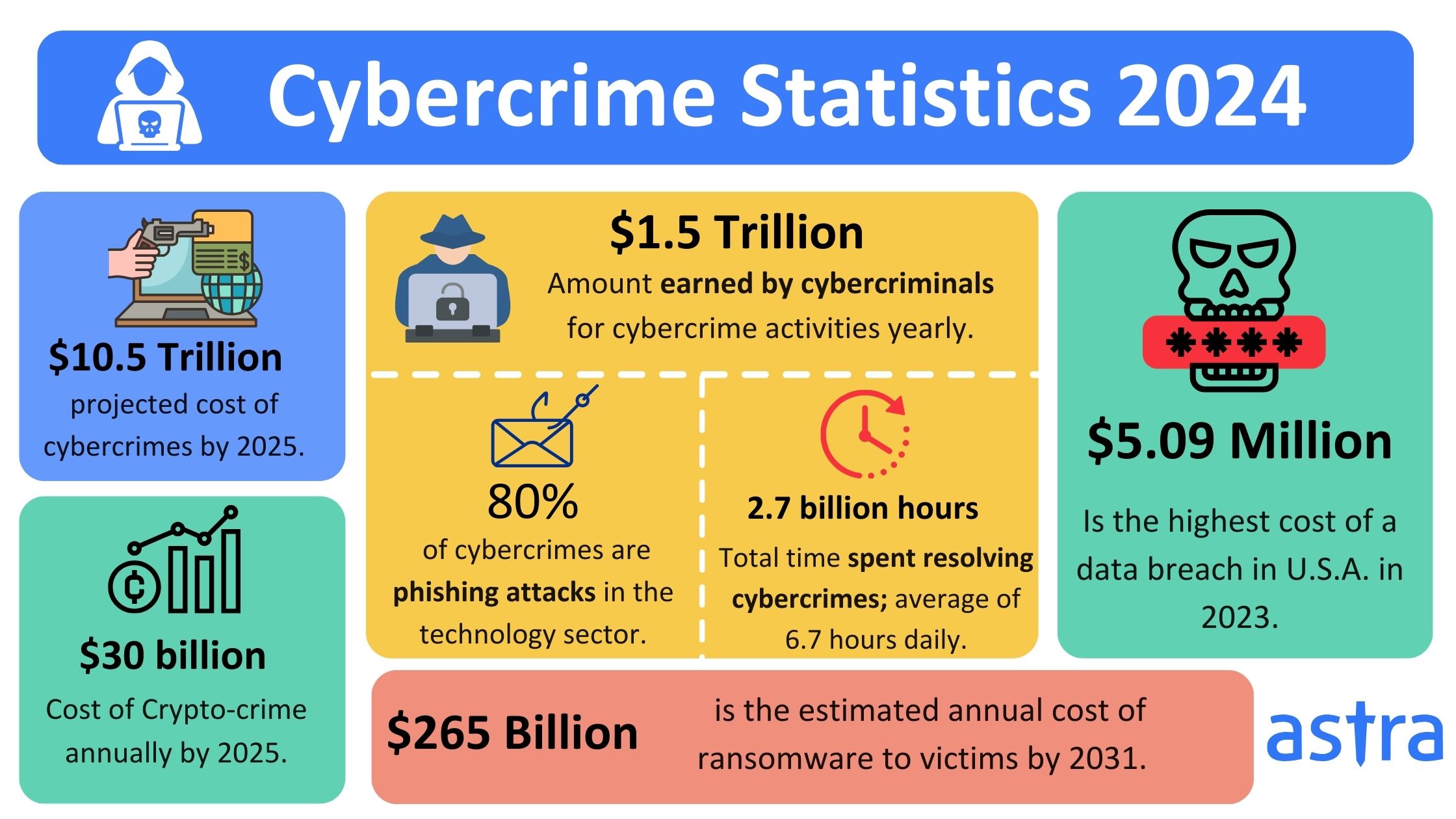
The world of cryptocurrency is in constant flux. As adoption grows and technology evolves, so too do the methods employed by those seeking to exploit the system. Predicting the future of crypto crime is a complex task, but by analyzing current trends, technological advancements, and regulatory developments, we can paint a picture of what the landscape might look like in 2025. This article will delve into the potential crypto crime trends we might see, focusing on the drivers, methods, and potential countermeasures.
Drivers of Crypto Crime in 2025
Several key factors will contribute to the evolution of crypto crime by 2025:
-
Increased Adoption: As more individuals and institutions embrace cryptocurrencies, the potential target pool for criminals expands exponentially. Greater liquidity and mainstream acceptance make crypto a more attractive target.
-
Technological Advancements: New technologies like Layer-2 scaling solutions, decentralized finance (DeFi) protocols, and cross-chain bridges offer both opportunities and risks. Criminals will likely exploit vulnerabilities in these emerging technologies.
-
Regulatory Uncertainty: The patchwork of regulations across different jurisdictions creates opportunities for regulatory arbitrage. Criminals may seek out havens with lax enforcement to conduct illicit activities.
-
Geopolitical Factors: Economic instability, political unrest, and international sanctions can drive individuals and organizations to use cryptocurrencies for illicit purposes, such as evading sanctions or funding illegal activities.
-
Sophistication of Criminal Actors: Criminals are becoming more sophisticated in their understanding of blockchain technology and cybersecurity. They are increasingly employing advanced techniques to obfuscate their activities and evade detection.
Anticipated Crypto Crime Trends in 2025
Based on these drivers, here are some of the crypto crime trends we can expect to see in 2025:
-
DeFi Exploits:
- Flash Loan Attacks: These attacks, which involve manipulating the price of tokens using flash loans (uncollateralized loans), are likely to become more sophisticated. Attackers may use advanced algorithms and machine learning to identify and exploit vulnerabilities in DeFi protocols.
- Governance Attacks: As DeFi protocols become more decentralized, governance tokens will become increasingly valuable. Attackers may attempt to acquire enough governance tokens to manipulate voting outcomes and steal funds from the protocol.
- Smart Contract Vulnerabilities: Despite efforts to improve smart contract security, vulnerabilities will continue to be a major source of exploits. Attackers will focus on identifying and exploiting flaws in complex smart contracts to drain funds from DeFi platforms.
- Cross-Chain Bridge Exploits: Cross-chain bridges, which allow users to transfer assets between different blockchains, are a prime target for attackers. Exploiting vulnerabilities in these bridges can result in massive losses, as demonstrated by several high-profile attacks in recent years.
-
Ransomware Attacks:
- Increased Sophistication: Ransomware attacks will become more targeted and sophisticated, with attackers using advanced techniques to infiltrate systems and encrypt data.
- Double Extortion: Attackers will increasingly use double extortion tactics, which involve stealing sensitive data in addition to encrypting it. They will then threaten to release the data publicly if the ransom is not paid.
- Ransomware-as-a-Service (RaaS): The RaaS model will continue to grow, allowing less technically skilled criminals to launch ransomware attacks.
- Targeting of Crypto Infrastructure: Attackers may target critical crypto infrastructure, such as exchanges and wallets, to disrupt the ecosystem and extort large sums of money.
-
Money Laundering:
- Decentralized Exchanges (DEXs): DEXs, which allow users to trade cryptocurrencies without intermediaries, will become increasingly popular for money laundering. The lack of KYC/AML requirements on many DEXs makes them attractive to criminals.
- Privacy Coins: Privacy coins, such as Monero and Zcash, will continue to be used for money laundering due to their enhanced privacy features.
- Mixing Services: Mixing services, which obfuscate the origin of cryptocurrencies, will become more sophisticated and harder to trace.
- Cross-Border Transactions: Criminals will continue to use cryptocurrencies to move funds across borders, evading traditional financial controls.
- Use of NFTs: laundering money through NFTs and manipulating the market.
-
Fraud and Scams:
- Pump-and-Dump Schemes: These schemes, which involve artificially inflating the price of a cryptocurrency and then selling it for a profit, will continue to be a problem.
- Rug Pulls: Rug pulls, which involve developers abandoning a project after raising funds from investors, will remain a common scam.
- Phishing Attacks: Phishing attacks, which involve tricking users into revealing their private keys or other sensitive information, will become more sophisticated and targeted.
- Impersonation Scams: Scammers will impersonate legitimate crypto companies or individuals to trick users into sending them money.
- AI-Driven Scams: With the rise of artificial intelligence, scammers may use AI to create convincing fake identities, generate realistic-sounding audio or video, and automate phishing attacks.
-
Sanctions Evasion:
- Use of Alternative Cryptocurrencies: Individuals and organizations subject to sanctions may use alternative cryptocurrencies to evade detection.
- Decentralized Infrastructure: Sanctioned entities may rely on decentralized infrastructure, such as DEXs and privacy coins, to circumvent traditional financial controls.
- Geographic Arbitrage: Sanctioned entities may exploit regulatory loopholes in different jurisdictions to move funds and conduct transactions.
Countermeasures and Mitigation Strategies
To combat these emerging crypto crime trends, several countermeasures and mitigation strategies will be essential:
-
Enhanced Regulatory Frameworks:
- Clear and Consistent Regulations: Governments need to establish clear and consistent regulations for cryptocurrencies to provide legal certainty and prevent regulatory arbitrage.
- KYC/AML Requirements: Exchanges and other crypto service providers should implement robust KYC/AML requirements to prevent money laundering and other illicit activities.
- International Cooperation: International cooperation is essential to combat cross-border crypto crime. Governments need to share information and coordinate enforcement efforts.
-
Technological Solutions:
- Blockchain Analytics: Blockchain analytics tools can be used to track and analyze cryptocurrency transactions, identify suspicious activity, and trace the flow of illicit funds.
- Smart Contract Audits: Regular audits of smart contracts can help identify and fix vulnerabilities before they can be exploited by attackers.
- Security Best Practices: Crypto companies should implement strong security best practices to protect their systems and data from cyberattacks.
- AI-Powered Threat Detection: Artificial intelligence can be used to detect and respond to crypto crime in real-time. AI algorithms can analyze transaction patterns, identify suspicious behavior, and flag potentially fraudulent activities.
-
Education and Awareness:
- User Education: Users need to be educated about the risks of crypto crime and how to protect themselves from scams and attacks.
- Industry Training: Crypto companies should provide training to their employees on how to identify and prevent crypto crime.
- Public Awareness Campaigns: Governments and industry organizations should launch public awareness campaigns to educate the public about the risks of crypto crime.
-
Collaboration and Information Sharing:
- Public-Private Partnerships: Governments and private sector companies should work together to combat crypto crime.
- Information Sharing Platforms: Information sharing platforms can be used to share threat intelligence and best practices among industry participants.
- Law Enforcement Cooperation: Law enforcement agencies need to work together to investigate and prosecute crypto criminals.
Conclusion
The crypto crime landscape in 2025 is likely to be characterized by increased sophistication, technological innovation, and regulatory complexity. By understanding the drivers of crypto crime and anticipating emerging trends, we can develop effective countermeasures and mitigation strategies to protect the crypto ecosystem. Enhanced regulatory frameworks, technological solutions, education and awareness, and collaboration and information sharing will be essential to combat crypto crime and ensure the long-term viability of cryptocurrencies. As the industry matures, a proactive and adaptive approach to security and compliance will be critical to fostering trust and confidence in the digital asset space.

