“Best Practices for Crypto Custody: Protecting Your Digital Assets
Related Articles Best Practices for Crypto Custody: Protecting Your Digital Assets
- Cosmos: An Internet Of Blockchains
- Move Data To Cloud
- Google Maps: Navigating The World, One Click At A Time
- What Is An NFT? A Deep Dive Into Non-Fungible Tokens
- Trading Volume: A Comprehensive Guide For Traders
Introduction
With great enthusiasm, let’s explore interesting topics related to Best Practices for Crypto Custody: Protecting Your Digital Assets. Come on knit interesting information and provide new insights to readers.
Table of Content
Best Practices for Crypto Custody: Protecting Your Digital Assets

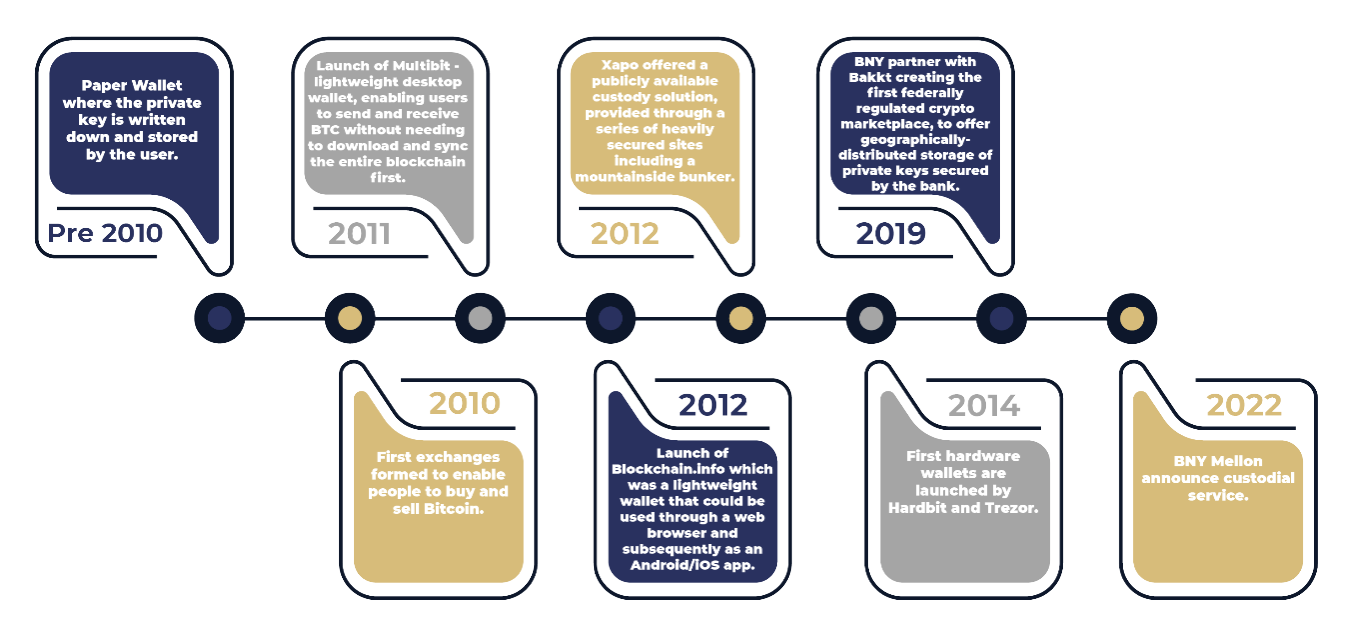
In the rapidly evolving world of cryptocurrencies, securing digital assets is paramount. Crypto custody, the practice of securely storing and managing private keys that control access to cryptocurrencies, is a critical aspect of this security. Whether you’re an individual investor, a financial institution, or a business, understanding and implementing best practices for crypto custody is essential to protect your investments and maintain trust in the digital asset ecosystem.
Why Crypto Custody Matters
Unlike traditional assets held by banks or brokerages, cryptocurrencies are decentralized and require individuals or institutions to manage their own security. This responsibility falls on the custodian, who must safeguard the private keys that authorize transactions. If these keys are lost, stolen, or compromised, the associated cryptocurrency is effectively lost forever.
The stakes are high. Cryptocurrency theft and fraud are on the rise, targeting both individuals and businesses. A robust crypto custody strategy is not just about preventing losses; it’s about building confidence in the digital asset space and fostering its long-term growth.
Key Principles of Crypto Custody
Effective crypto custody rests on several core principles:
-
Security First: Security should be the primary consideration in every aspect of custody. This includes physical security, cybersecurity, and procedural safeguards.
-
Segregation of Duties: No single individual should have complete control over the custody process. Separating responsibilities reduces the risk of internal fraud or error.
-
Redundancy and Backup: Multiple layers of redundancy and secure backups are essential to prevent data loss or system failures.
-
Auditability: Custody systems should be auditable, with clear records of all transactions and access logs.
-
Compliance: Custodians must comply with relevant regulations and industry standards, which vary by jurisdiction.
-
Risk Management: A comprehensive risk management framework should identify, assess, and mitigate potential threats to digital assets.
Types of Crypto Custody Solutions
Choosing the right custody solution depends on your specific needs and risk tolerance. Here are some common options:
-
Self-Custody: Individuals manage their own private keys, typically using hardware wallets, software wallets, or paper wallets. This approach offers maximum control but requires a high level of technical expertise and responsibility.
-
Third-Party Custodians: Specialized companies provide custody services for a fee. These custodians offer enhanced security, insurance, and compliance features, but they also introduce a level of counterparty risk.
-
Multi-Party Computation (MPC): This cryptographic technique distributes private keys across multiple parties, requiring a threshold of parties to cooperate in order to authorize transactions. MPC reduces the risk of a single point of failure.
-
Hardware Security Modules (HSMs): HSMs are tamper-proof hardware devices that store and manage private keys. They provide a high level of physical security and are often used by institutions.
-
Cold Storage: Storing private keys offline, away from internet-connected devices, significantly reduces the risk of hacking. Cold storage is often combined with other custody methods.
Best Practices for Secure Crypto Custody
Here’s a detailed breakdown of best practices across various aspects of crypto custody:
1. Private Key Management
- Key Generation: Generate private keys using strong, cryptographically secure methods. Avoid using online key generators or weak passwords.
- Key Storage: Store private keys in a secure location, such as a hardware wallet, HSM, or offline cold storage.
- Key Backup: Create multiple, geographically distributed backups of your private keys. Encrypt backups to protect against unauthorized access.
- Key Rotation: Periodically rotate your private keys to reduce the risk of compromise.
- Access Control: Implement strict access controls to limit who can access private keys. Use multi-factor authentication (MFA) for all access points.
2. Hardware and Software Security
- Hardware Wallets: Use reputable hardware wallets that have been independently audited for security vulnerabilities.
- Software Wallets: Choose software wallets from trusted providers with a strong track record of security. Keep your software up to date with the latest security patches.
- Operating System Security: Use a secure operating system and keep it updated. Disable unnecessary services and applications.
- Firewalls: Implement firewalls to protect your network from unauthorized access.
- Antivirus Software: Install and maintain antivirus software to detect and remove malware.
- Endpoint Security: Secure all devices that access your custody system with endpoint detection and response (EDR) solutions.
3. Physical Security
- Secure Facilities: Store hardware wallets and other physical assets in secure facilities with limited access.
- Surveillance: Implement video surveillance and alarm systems to deter unauthorized access.
- Background Checks: Conduct thorough background checks on all employees who have access to custody systems.
- Access Control: Use physical access controls, such as biometric scanners or keycards, to restrict access to sensitive areas.
- Visitor Management: Implement a strict visitor management policy to track and control who enters your facilities.
4. Cybersecurity
- Network Segmentation: Segment your network to isolate critical custody systems from other parts of your organization.
- Intrusion Detection and Prevention: Deploy intrusion detection and prevention systems (IDS/IPS) to monitor network traffic for malicious activity.
- Vulnerability Management: Regularly scan your systems for vulnerabilities and patch them promptly.
- Penetration Testing: Conduct periodic penetration testing to identify weaknesses in your security defenses.
- Incident Response: Develop and maintain an incident response plan to handle security breaches or other incidents.
- Security Awareness Training: Provide regular security awareness training to employees to educate them about phishing, social engineering, and other threats.
5. Operational Security
- Segregation of Duties: Separate responsibilities for key generation, transaction authorization, and audit.
- Multi-Signature Authorization: Require multiple approvals for transactions to prevent unauthorized transfers.
- Transaction Monitoring: Monitor all transactions for suspicious activity, such as large transfers or unusual patterns.
- Auditing: Conduct regular audits of your custody system to ensure compliance with security policies and procedures.
- Disaster Recovery: Develop and maintain a disaster recovery plan to ensure business continuity in the event of a system failure or natural disaster.
- Employee Training: Provide comprehensive training to all employees on custody procedures, security protocols, and regulatory requirements.
6. Compliance and Regulation
- Know Your Customer (KYC): Implement KYC procedures to verify the identity of your customers and prevent money laundering.
- Anti-Money Laundering (AML): Comply with AML regulations to detect and report suspicious transactions.
- Data Privacy: Protect the privacy of your customers’ data in accordance with applicable data privacy laws.
- Regulatory Reporting: Comply with all regulatory reporting requirements.
- Licensing: Obtain any necessary licenses or registrations to operate as a crypto custodian.
7. Insurance
- Custody Insurance: Obtain insurance coverage to protect against the loss of digital assets due to theft, fraud, or other causes.
- Cyber Insurance: Obtain cyber insurance to cover the costs of responding to and recovering from cyberattacks.
Choosing a Crypto Custodian
If you choose to use a third-party custodian, consider the following factors:
- Security Practices: Evaluate the custodian’s security practices, including their key management, physical security, and cybersecurity measures.
- Compliance: Ensure the custodian is compliant with relevant regulations and industry standards.
- Insurance: Verify that the custodian has adequate insurance coverage.
- Reputation: Research the custodian’s reputation and track record.
- Fees: Compare the custodian’s fees with those of other providers.
- Auditability: Ensure the custodian’s systems are auditable.
- Technology: Assess the custodian’s technology platform and its ability to support your needs.
Conclusion
Crypto custody is a complex and evolving field. By implementing these best practices, individuals and institutions can significantly reduce the risk of loss and protect their digital assets. Whether you choose self-custody or a third-party solution, a strong focus on security, compliance, and risk management is essential for success in the digital asset space.