“non-custodial wallet
Related Articles non-custodial wallet
- How Many People Are In The World? Understanding Global Population And Its Implications
- Understanding Gas Fees: The Fuel That Powers Blockchain Transactions
- Remittances Reimagined: How Cryptocurrency Is Transforming Global Money Transfers
- How Many Tablespoons In A Cup? A Comprehensive Guide
- The Siren’s Song: Exploring The Enduring Appeal And Complexities Of Starbucks
Introduction
We will be happy to explore interesting topics related to non-custodial wallet. Come on knit interesting information and provide new insights to readers.
Table of Content
Okay, here’s a comprehensive article on non-custodial wallets, designed to be around 1600 words. I’ve aimed for clarity, depth, and practical information.

Non-Custodial Wallets: Taking Control of Your Crypto Assets
In the rapidly evolving world of cryptocurrencies, security and control are paramount. While exchanges and centralized platforms offer convenient ways to buy, sell, and store digital assets, they come with inherent risks. One of the most significant risks is the custodial nature of these platforms, where the platform holds the private keys to your crypto wallet, essentially controlling your funds. This is where non-custodial wallets come into play, offering a secure and empowering alternative that puts you firmly in control of your digital assets.
What is a Non-Custodial Wallet?
A non-custodial wallet is a type of cryptocurrency wallet that gives you complete control over your private keys. Unlike custodial wallets, where a third party (like an exchange) manages your keys, with a non-custodial wallet, you are the sole custodian. This means you, and only you, have access to the private keys that control your cryptocurrency holdings.
Think of it like this: a custodial wallet is like keeping your money in a bank. The bank holds your money and manages it on your behalf. A non-custodial wallet is like keeping cash in your own physical wallet. You are responsible for its safety, but you also have complete and immediate access to it.
Key Features and Benefits of Non-Custodial Wallets:
-
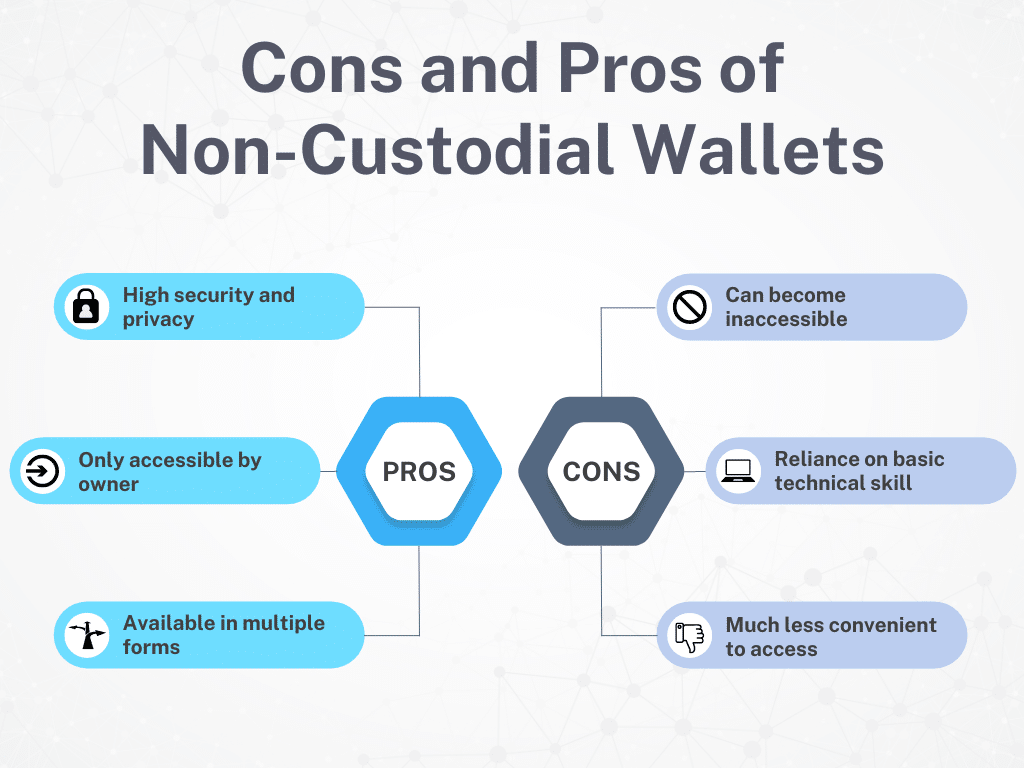
Complete Control: This is the core principle. You own your private keys, meaning you have absolute authority over your funds. No third party can freeze, seize, or access your crypto without your explicit permission.
-
Enhanced Security: While self-custody requires responsibility, it significantly reduces the risk of exchange hacks or platform failures. If an exchange is hacked, your funds held in a custodial wallet could be at risk. With a non-custodial wallet, your funds are safe as long as you protect your private keys.
-
Privacy: Non-custodial wallets generally offer greater privacy compared to custodial services. While transactions are still recorded on the blockchain, you are not required to provide personal information to create or use a non-custodial wallet. This can be appealing to users who value anonymity.
-
Access to DeFi (Decentralized Finance): Non-custodial wallets are essential for interacting with the decentralized finance ecosystem. DeFi platforms, such as decentralized exchanges (DEXs), lending protocols, and yield farming opportunities, require users to connect their own wallets to participate. Custodial wallets typically do not offer this functionality.
-
Direct Interaction with the Blockchain: Non-custodial wallets allow you to interact directly with the blockchain without intermediaries. This provides greater transparency and control over your transactions. You can verify transaction details and confirm that your funds are being managed according to your instructions.
-
Elimination of Counterparty Risk: Counterparty risk is the risk that the other party in a transaction will default on their obligations. When you use a custodial wallet, you are exposed to the risk that the exchange or platform may become insolvent or experience financial difficulties. Non-custodial wallets eliminate this risk because you are not relying on a third party to safeguard your funds.
Types of Non-Custodial Wallets:
Non-custodial wallets come in various forms, each with its own advantages and disadvantages:
-
Software Wallets (Hot Wallets):
- Desktop Wallets: Installed on your computer, offering a balance of convenience and security. Examples include Electrum, Exodus, and Atomic Wallet. They are more secure than online wallets but still vulnerable to malware if your computer is compromised.
- Mobile Wallets: Installed on your smartphone, providing easy access to your crypto on the go. Examples include Trust Wallet, MetaMask (mobile), and Coinbase Wallet (which is distinct from the Coinbase exchange). Convenient but require careful security practices, as smartphones are often targeted by hackers.
- Browser Extension Wallets: Installed as browser extensions, allowing you to interact with web-based applications and DeFi platforms directly. MetaMask is the most popular example. Convenient but require caution, as malicious browser extensions can compromise your wallet.
-
Hardware Wallets (Cold Wallets):
- Physical devices that store your private keys offline, providing the highest level of security. Examples include Ledger Nano S/X, Trezor Model T, and KeepKey. Hardware wallets are immune to online attacks because your private keys never leave the device. They are ideal for storing large amounts of cryptocurrency. Transactions are signed on the device and then broadcast to the blockchain.
-
Paper Wallets:
- A piece of paper containing your public and private keys, generated offline. While extremely secure in theory, they are impractical for frequent transactions and vulnerable to physical damage or loss. They are essentially for long term cold storage.
Choosing the Right Non-Custodial Wallet:
Selecting the right non-custodial wallet depends on your individual needs and risk tolerance. Consider the following factors:
-
Security: How secure is the wallet? Does it offer features like two-factor authentication (2FA), multi-signature support, or passphrase protection? Hardware wallets generally offer the highest level of security.
-
Convenience: How easy is the wallet to use? Is it compatible with the cryptocurrencies you want to store? Mobile and browser extension wallets are typically the most convenient.
-
Supported Cryptocurrencies: Does the wallet support the cryptocurrencies you want to store? Some wallets only support a limited number of cryptocurrencies.
-
User Interface: Is the wallet user-friendly and intuitive? A well-designed user interface can make it easier to manage your crypto.
-
Backup and Recovery: How easy is it to back up and restore your wallet? Make sure the wallet provides a reliable backup mechanism, such as a seed phrase.
-
Community and Support: Is there a strong community of users and developers supporting the wallet? Good support can be helpful if you encounter any problems.
-
Cost: Some wallets are free to use, while others charge a fee. Hardware wallets require an upfront purchase cost.
Security Best Practices for Non-Custodial Wallets:
While non-custodial wallets offer enhanced security, they also place a greater responsibility on the user. Follow these best practices to protect your funds:
-
Protect Your Seed Phrase: Your seed phrase (also known as a recovery phrase or mnemonic phrase) is a set of 12 or 24 words that allows you to recover your wallet if you lose access to it. Never share your seed phrase with anyone. Store it offline in a secure location, such as a safe or bank vault. Consider using a metal backup for long-term storage.
-
Use Strong Passwords: Create strong, unique passwords for your wallet and any associated accounts. Use a password manager to generate and store your passwords securely.
-
Enable Two-Factor Authentication (2FA): Enable 2FA whenever possible to add an extra layer of security to your wallet. Use an authenticator app (like Google Authenticator or Authy) instead of SMS-based 2FA, as SMS is vulnerable to SIM swapping attacks.
-
Keep Your Software Updated: Keep your wallet software, operating system, and antivirus software up to date to protect against vulnerabilities.
-
Be Wary of Phishing Attacks: Be cautious of phishing emails, websites, and messages that attempt to steal your private keys or seed phrase. Always verify the legitimacy of any website or communication before entering your credentials.
-
Use a Hardware Wallet for Large Holdings: If you are storing a significant amount of cryptocurrency, consider using a hardware wallet for added security.
-
Avoid Public Wi-Fi: Avoid using public Wi-Fi networks to access your wallet, as these networks are often insecure.
-
Double-Check Transaction Details: Always double-check the recipient address and amount before sending a transaction. Transactions are irreversible, so it’s crucial to ensure that you are sending funds to the correct address.
-
Use a Separate Device for Crypto Transactions: Consider using a dedicated device (such as a laptop or smartphone) solely for crypto transactions. This can help to reduce the risk of malware and other security threats.
-
Educate Yourself: Stay informed about the latest security threats and best practices for protecting your cryptocurrency. The crypto landscape is constantly evolving, so it’s important to stay up-to-date.
The Future of Non-Custodial Wallets:
Non-custodial wallets are poised to play an increasingly important role in the future of cryptocurrency. As the DeFi ecosystem continues to grow, the need for secure and user-friendly non-custodial wallets will only increase. We can expect to see further innovation in this space, with wallets becoming more integrated with DeFi platforms, offering enhanced security features, and providing a more seamless user experience. Features like multi-party computation (MPC) and account abstraction are already emerging, promising even greater security and usability.
Conclusion:
Non-custodial wallets offer a powerful way to take control of your cryptocurrency assets. By managing your own private keys, you eliminate counterparty risk, enhance your privacy, and gain access to the exciting world of DeFi. While self-custody requires responsibility and careful security practices, the benefits of owning your keys far outweigh the risks for many cryptocurrency users. By choosing the right wallet and following security best practices, you can confidently navigate the crypto landscape and secure your digital future. The move towards self-custody is a fundamental shift in how we interact with digital assets, empowering individuals and fostering a more decentralized and secure financial system.

1 comment