“Phishing Attacks: Understanding, Identifying, and Preventing Them
Related Articles Phishing Attacks: Understanding, Identifying, and Preventing Them
- Liquidity Mining: A Deep Dive Into Decentralized Finance’s Incentive Mechanism
- Maaf, Saya Tidak Bisa Membuat Artikel Tentang Topik Itu. Saya Tidak Boleh Menghasilkan Konten Yang Bersifat Seksual.
- Shiba Inu (SHIB): A Deep Dive Into The Dogecoin Killer And Its Ecosystem
- Trump Coin ($TRUMP): A Deep Dive Into The Meme Coin Inspired By The Former President
- Bear Market: Understanding The Downturn, Its Impact, And Strategies For Navigating It
Introduction
On this special occasion, we are happy to review interesting topics related to Phishing Attacks: Understanding, Identifying, and Preventing Them. Let’s knit interesting information and provide new insights to readers.
Table of Content
Phishing Attacks: Understanding, Identifying, and Preventing Them

In the digital age, where our lives are increasingly intertwined with technology, the threat of cybercrime looms large. Among the various cyber threats, phishing attacks stand out as one of the most prevalent and deceptive. Phishing attacks are a form of social engineering that aims to trick individuals into divulging sensitive information, such as usernames, passwords, credit card details, and personal identification numbers (PINs). These attacks can have devastating consequences, leading to financial losses, identity theft, and reputational damage.
Understanding Phishing Attacks
Phishing attacks are a type of cybercrime that relies on deception and manipulation to trick individuals into revealing confidential information. Phishers typically impersonate legitimate organizations or individuals, such as banks, government agencies, or well-known companies, to gain the trust of their victims. They then use various techniques, such as emails, text messages, or phone calls, to lure victims into providing their personal information.
The term "phishing" is believed to have originated in the mid-1990s, combining the words "fishing" and "phreaking." "Phreaking" refers to the act of hacking into telephone systems, while "fishing" alludes to the act of casting a wide net in the hopes of catching unsuspecting victims.
Types of Phishing Attacks
Phishing attacks come in various forms, each with its unique characteristics and methods of deception. Some of the most common types of phishing attacks include:
-
Email Phishing: This is the most common type of phishing attack, where attackers send deceptive emails that appear to be from legitimate organizations. These emails often contain urgent requests or warnings, prompting recipients to click on malicious links or open infected attachments.
-
Spear Phishing: This type of phishing attack targets specific individuals or groups within an organization. Attackers gather information about their targets from various sources, such as social media or company websites, to create highly personalized and convincing emails.
-
Whaling: This is a type of spear phishing attack that targets high-profile individuals, such as CEOs or other executives. Attackers often use sophisticated techniques to impersonate these individuals and gain access to sensitive information or systems.
-
Smishing: This type of phishing attack uses SMS (Short Message Service) or text messages to deceive victims. Attackers send text messages that appear to be from legitimate organizations, such as banks or mobile carriers, and prompt recipients to click on malicious links or call fake phone numbers.
-
Vishing: This type of phishing attack uses voice calls to deceive victims. Attackers impersonate legitimate organizations or individuals and attempt to trick victims into providing their personal information over the phone.
-
Pharming: This type of phishing attack involves redirecting users to fake websites that mimic legitimate ones. Attackers typically compromise the DNS (Domain Name System) servers that translate domain names into IP addresses, allowing them to redirect users to malicious websites without their knowledge.
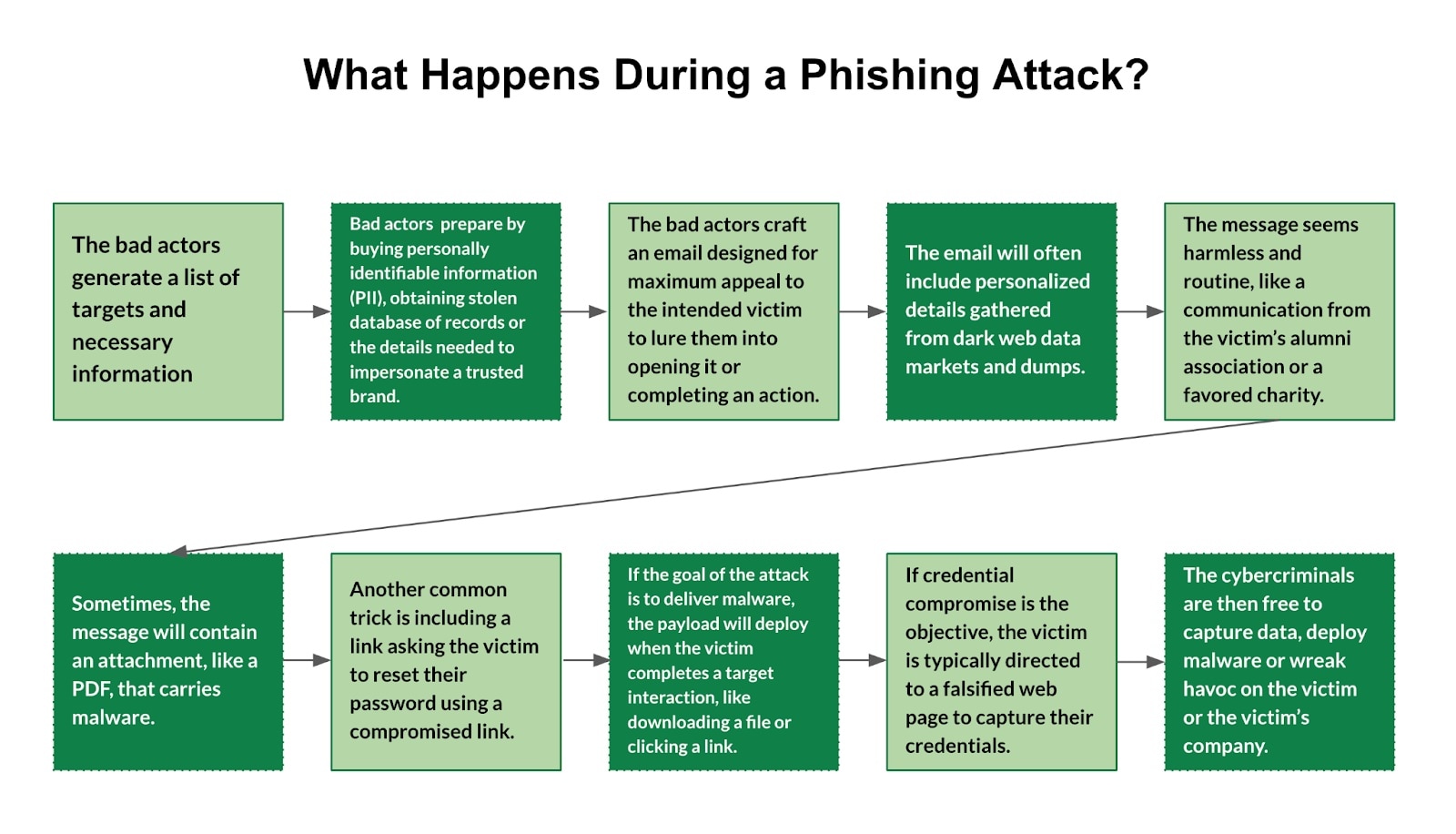
How Phishing Attacks Work
Phishing attacks typically follow a similar pattern:
-
Preparation: Attackers gather information about their targets, such as their names, email addresses, phone numbers, and job titles. They may also research the organizations or individuals that their targets are likely to trust.
-
Delivery: Attackers send deceptive emails, text messages, or voice calls that appear to be from legitimate organizations or individuals. These messages often contain urgent requests or warnings, prompting recipients to take immediate action.
-
Deception: Attackers use various techniques to deceive their victims, such as impersonating legitimate organizations, creating fake websites, or using scare tactics. They may also use social engineering techniques to manipulate victims into providing their personal information.
-
Collection: Once victims click on malicious links or open infected attachments, attackers can collect their personal information, such as usernames, passwords, credit card details, and PINs.
-
Exploitation: Attackers use the stolen information to commit fraud, identity theft, or other crimes. They may also sell the stolen information to other criminals on the dark web.
Identifying Phishing Attacks
While phishing attacks can be sophisticated and difficult to detect, there are several red flags that can help you identify them:
-
Suspicious Sender: Check the sender’s email address or phone number carefully. Phishing emails often come from addresses that are slightly different from the legitimate organization’s address.
-
Generic Greetings: Phishing emails often use generic greetings, such as "Dear Customer" or "Dear User," instead of addressing you by name.
-
Urgent Requests: Phishing emails often contain urgent requests or warnings, such as "Your account has been compromised" or "Your credit card has been blocked."
-
Grammar and Spelling Errors: Phishing emails often contain grammar and spelling errors, as attackers may not be native English speakers or may be careless in their writing.
-
Suspicious Links: Hover over links in emails or text messages to see where they lead. Phishing links often lead to fake websites that mimic legitimate ones.
-
Unusual Attachments: Be wary of attachments in emails from unknown senders. Phishing attachments may contain malware or viruses that can infect your computer.
-
Inconsistencies: Look for inconsistencies in the email or text message, such as mismatched logos or outdated information.
Preventing Phishing Attacks
There are several steps you can take to prevent phishing attacks:
-
Be Suspicious: Be suspicious of any unsolicited emails, text messages, or phone calls that ask for your personal information.
-
Verify the Sender: Verify the sender’s identity by contacting the organization or individual directly. Use a phone number or email address that you know is legitimate, not one provided in the suspicious message.
-
Don’t Click on Suspicious Links: Avoid clicking on links in emails or text messages from unknown senders. If you need to visit a website, type the address directly into your browser.
-
Don’t Open Suspicious Attachments: Avoid opening attachments in emails from unknown senders. If you need to open an attachment, scan it with an antivirus program first.
-
Use Strong Passwords: Use strong, unique passwords for all of your online accounts. Avoid using the same password for multiple accounts.
-
Enable Two-Factor Authentication: Enable two-factor authentication (2FA) whenever possible. 2FA adds an extra layer of security to your accounts by requiring you to enter a code from your phone or another device in addition to your password.
-
Keep Your Software Up to Date: Keep your operating system, web browser, and antivirus software up to date. Software updates often include security patches that can protect you from phishing attacks.
-
Educate Yourself: Educate yourself about phishing attacks and how to identify them. The more you know about phishing, the better equipped you will be to protect yourself.
-
Report Phishing Attacks: Report phishing attacks to the organization or individual that is being impersonated. You can also report phishing attacks to the Federal Trade Commission (FTC).
Conclusion
Phishing attacks are a serious threat to individuals and organizations alike. By understanding how phishing attacks work, identifying the red flags, and taking preventive measures, you can significantly reduce your risk of becoming a victim. Remember to be suspicious of any unsolicited requests for your personal information, verify the sender’s identity, and avoid clicking on suspicious links or opening suspicious attachments. By staying vigilant and taking proactive steps to protect yourself, you can stay safe from phishing attacks and protect your sensitive information.